Introduction
Delivery is an easy, Linux box made by Ippsec and hosted on Hack The Box. Hacking Delivery requires little technical knowledge or reliance on tools, which makes it great for beginners. Hacking in requires:
- Exploiting logic errors;
- MySQL enumeration; and
- Hashcat.
Enumeration
Whilst I started this box with my usual AutoRecon and Nmap scans, I actually didn’t look at the output to hack in. While those scans were running I started up Chrome and visited http://delivery.htb, after already adding the required line to my /etc/hosts file.
Port 80
This page didn’t reveal much other than a “Contact Us” page so I followed the link.
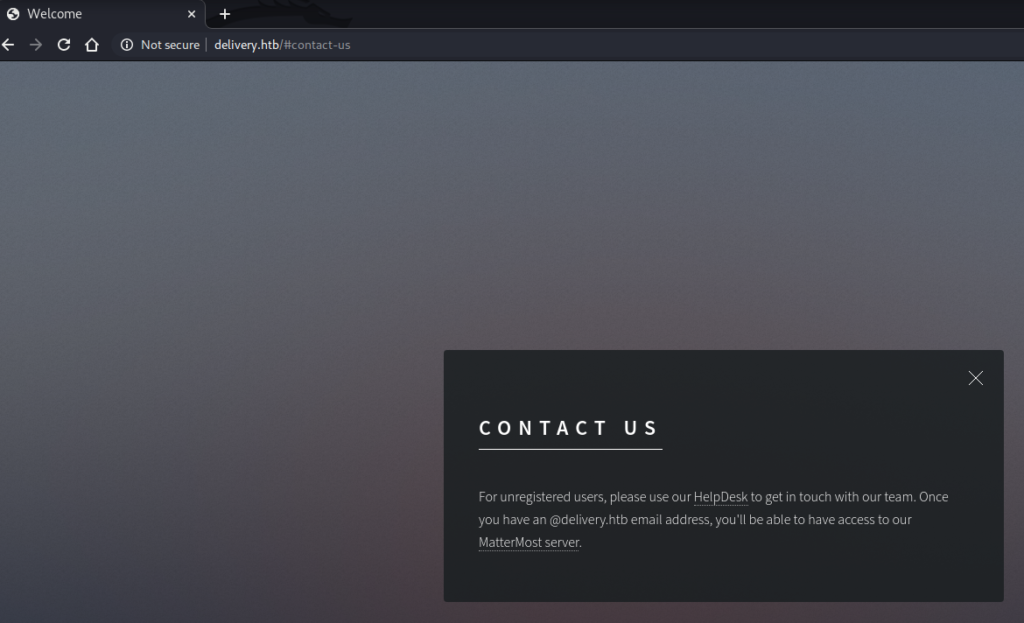
This page revealed two links:
- a link to a helpdesk subdomain (http://helpdesk.delivery.htb);
- a link to a MatterMost server (http://delivery.htb:8065).
I opened both of these on separate tabs and decided to continue exploring the Helpdesk subdomain first.
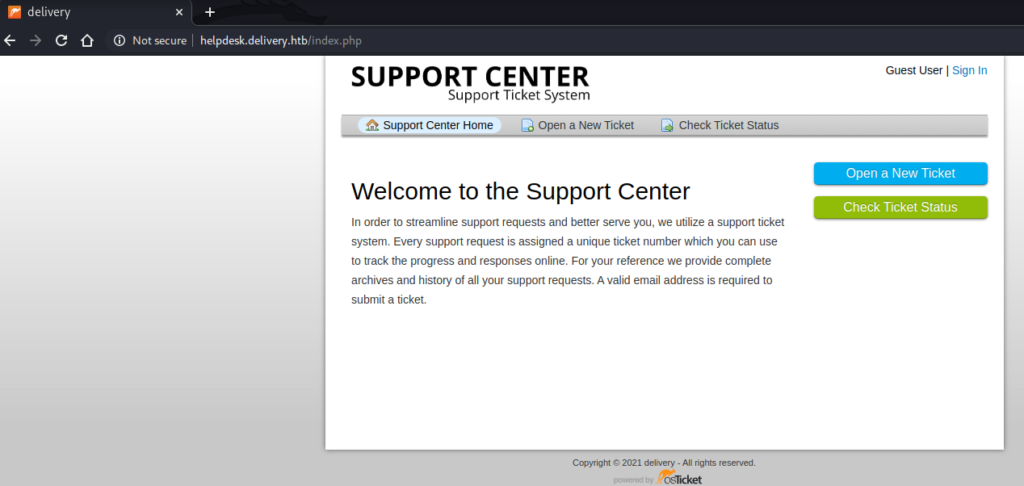
This page allows a user to perform a few functions:
- Register a user account;
- Submit a ticket as a register user or a guest; and
- View tickets they have submitted.
I tried to create an account but found it required email verification, which is not possible on Hack The Box boxes. Therefore I used a guest account to create a ticket and view that ticket.
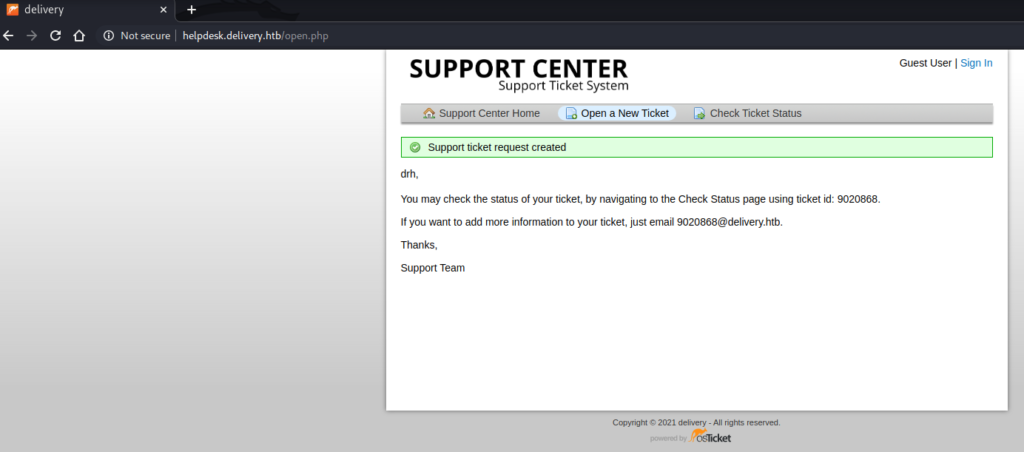
Once the ticket was submitted I could view it, add to it and edit it.
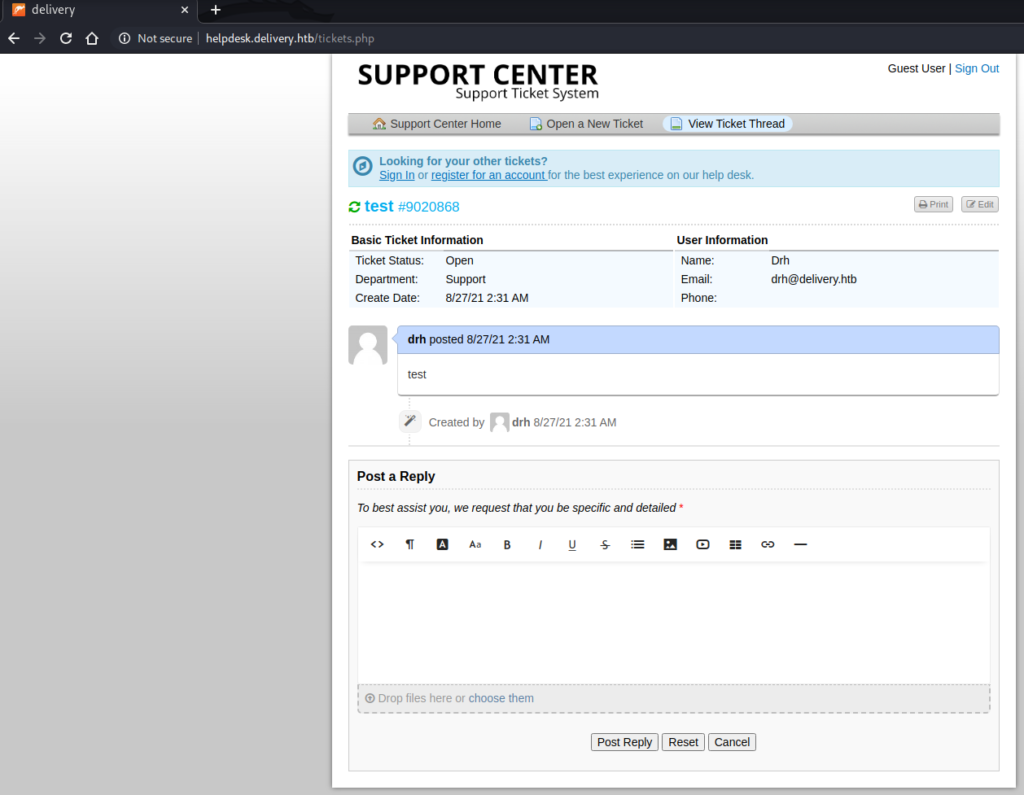
I tried several exploit techniques on this application, including:
- Various code injection attacks (SQL, HTML, etc);
- Malicious attachment attacks;
- Using Searchsploit and Google to find pre-compiled exploits (the application software is osTicket, shown on the bottom of the page);
- Further enumeration of the subdomain using tools such as Gobuster and ffuf; and
- LFI and RFI attacks.
However all of these attacks were unsuccessful, so I decided to walk away from this page and explore elsewhere. I started by visiting the other link on the “Contact Us” page, http://delivery.htb:8065.
Port 8065
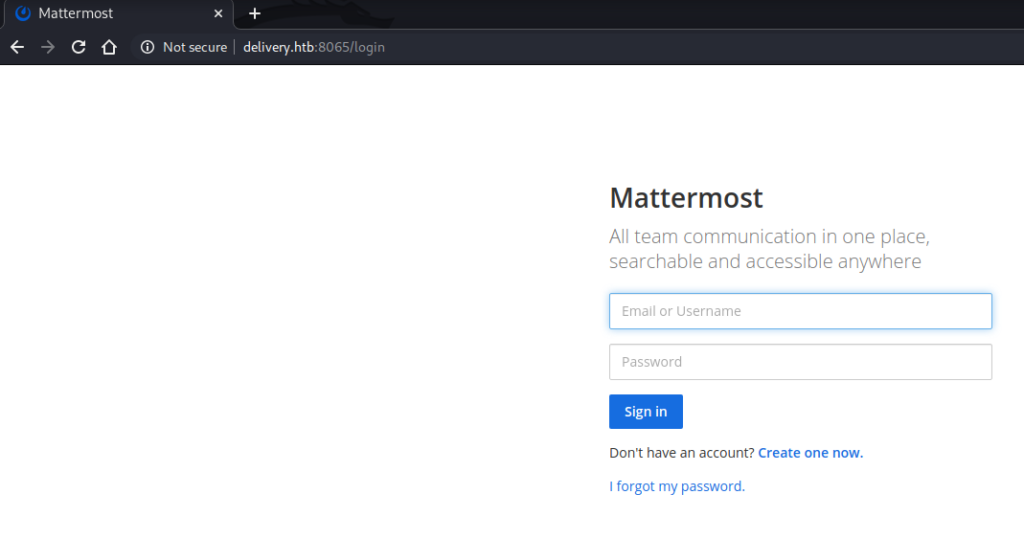
This link took me to a login page for the Mattermost application. I tried to create an account, but again the application required email verification.
I tried further enumeration, again using tools such as Searchsploit, Gobuster and ffuf, to find other pages, directories and subdomains, however they all returned empty. Because of this, I reasoned that there must be a way to either fool the email verification or successfully complete it and create an account. I started looking through my notes and found this screenshot from the helpdesk application:
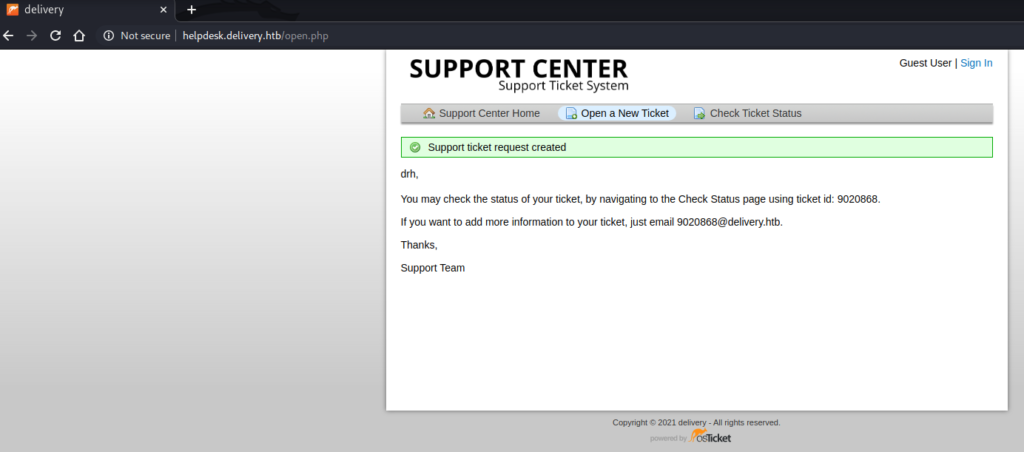
This screenshot had an email address listed: 9020868@delivery.htb. I signed up for an account at Mattermost using this email address and then visited the helpdesk to check if I had received the email.
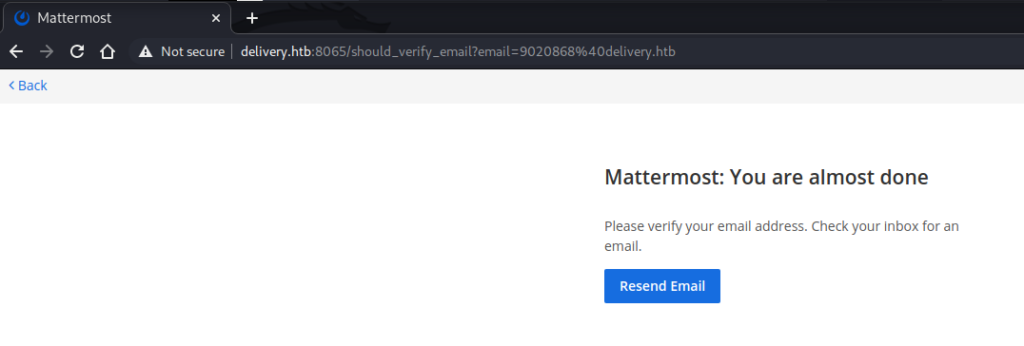
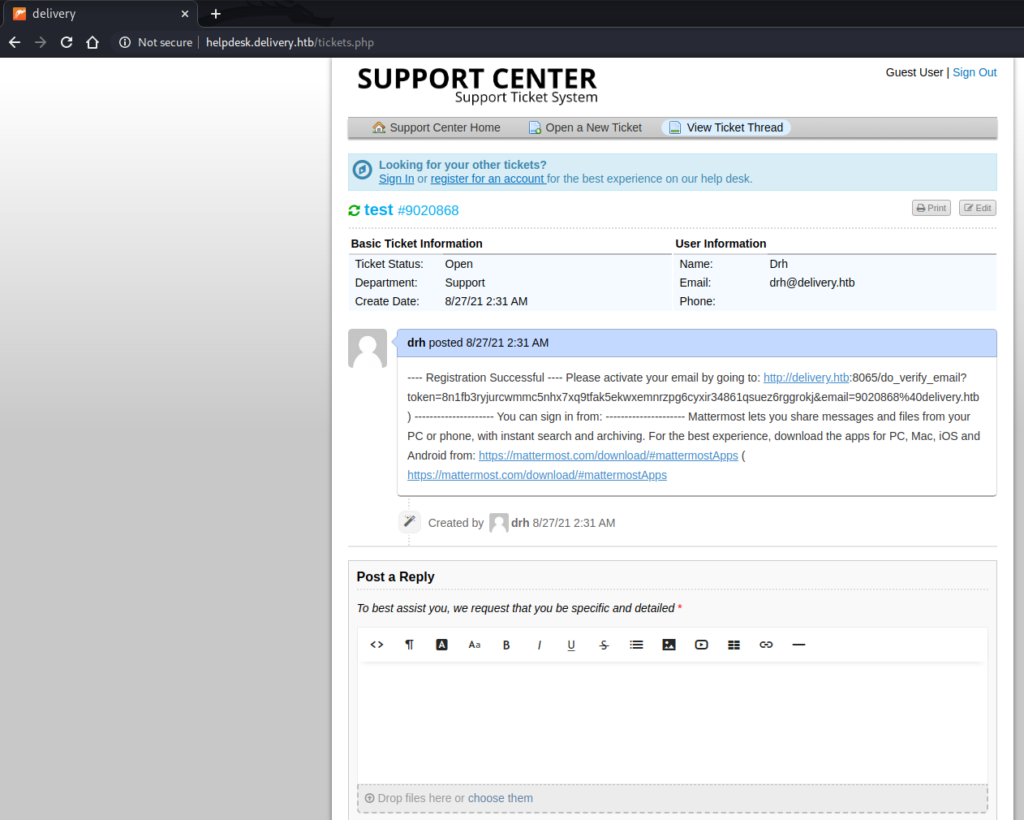
This attempt was successful and provided a link for me to verify my address.
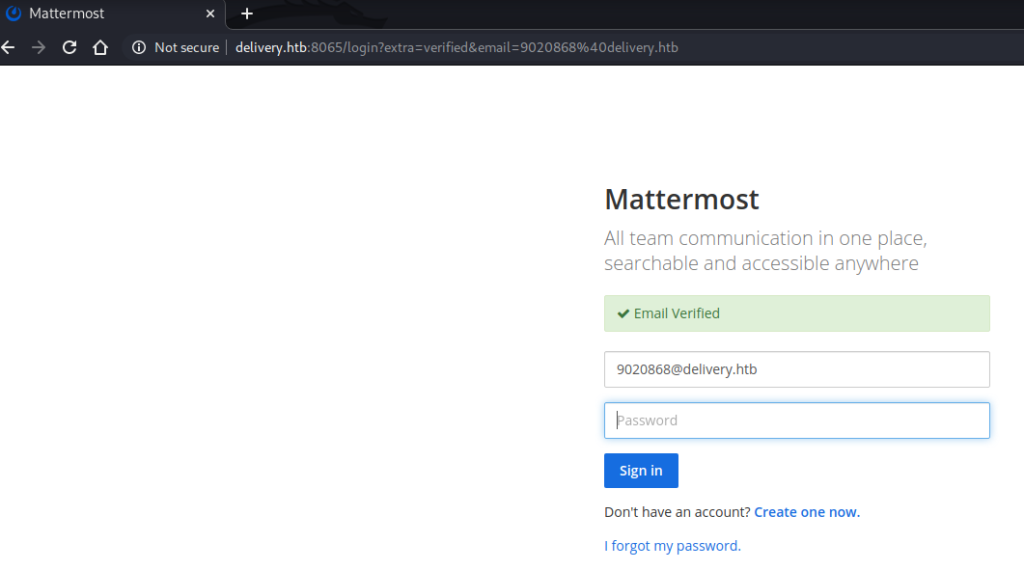
User
With my email verified I was able to sign in to Mattermost. The Mattermost dashboard was effectively a large messaging system, with only a couple of pre-set messages that immediately caught my eye:
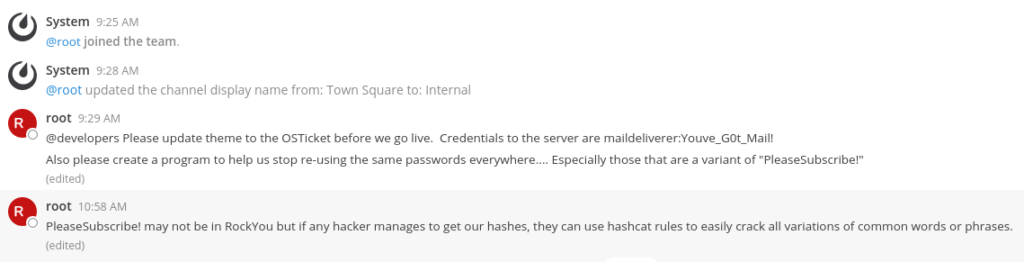
These messages very clearly signposted the way to root:
- Login as a low-level user with the credentials maildeliverer@delivery.htb:Youve_G0t_Mail!;
- Find a hash of the root password somewhere on the box;
- Crack that hash with hashcat using hashcat rules.
Therefore I used SSH to connect to the box with the maildeliverer account and grabbed the user flag.
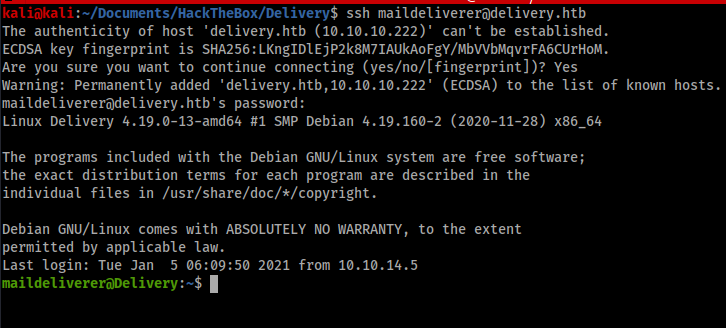
Privilege Escalation
Because of the clues provided on the Mattermost dashboard I was confident in my approach to privilege escalation. This meant I skipped most of my usual privilege escalation checks and immediately started looking around for credentials or some sort of hash. I knew there were at least two applications on the box, osTicket and Mattermost, so I started combing through these files for credentials.
I started in the ‘/var/www/’ directory and found the osTicket application but returned empty-handed. Next, I found the Mattermost application in the ‘/opt’ directory and in here I found my way forward:
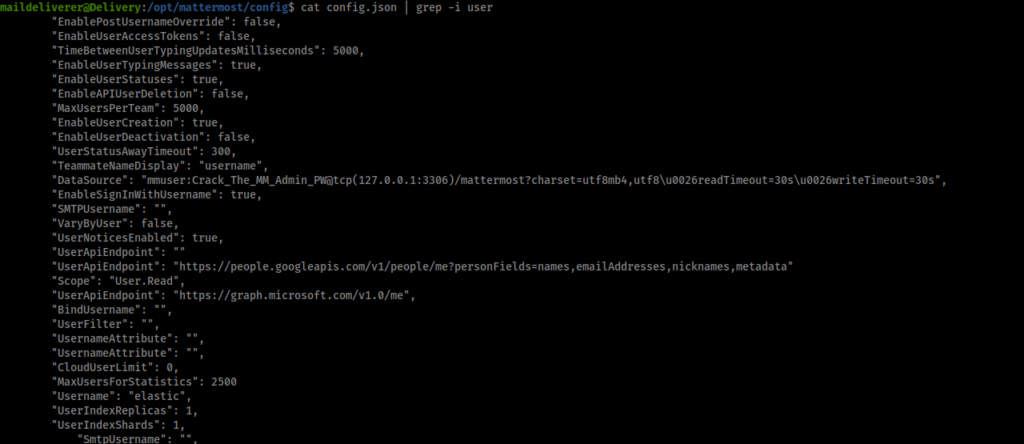
One of the configuration files in the Mattermost application contained the credentials ‘mmuser:Crack_The_MM_Admin_PW’ with a reference to ‘127.0.0.1:3306’. Therefore I used these credentials to log in to MySQL and continue searching for hashes.
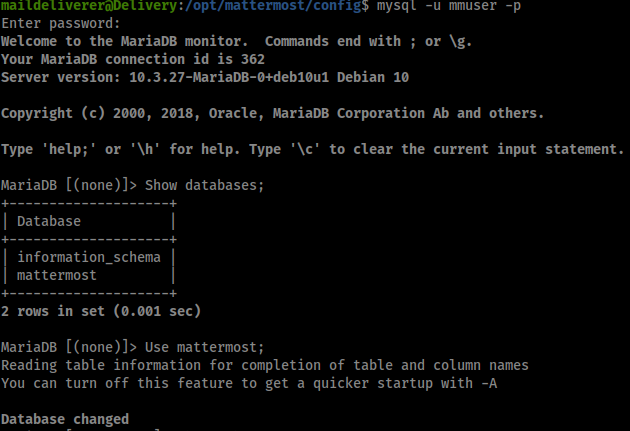
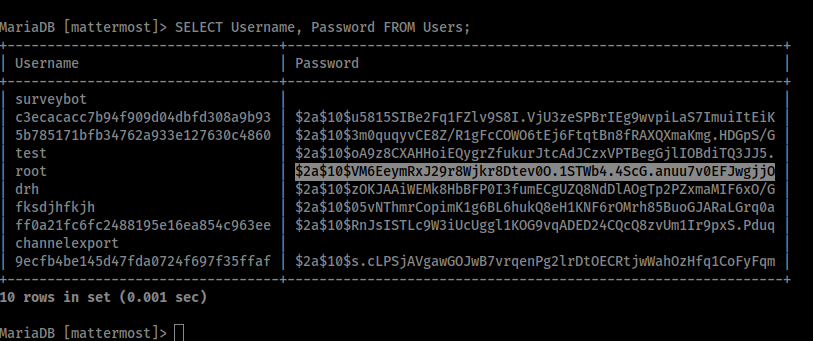
Finding the Users table and hash list was very straightforward. The obvious username that stood out the most was ‘root’, so I grabbed the corresponding hash and started up hashcat.
Hashcat
I have always preferred John The Ripper to hashcat, simply because I have used it more and feel more comfortable on it. However the hints on the Mattermost dashboard were very clear, so I took this as an opportunity to practice my hashcat skills. The hints mentioned two key points:
- The password was some variation of “PleaseSubscribe!”; and
- Additional hashcat rules would be required to crack the hash.
Another useful variable was the ‘$2a$’ prefix on the hash, which told me the password was hashed using bcrypt. What was still unknown was whether the variation would be something as simple as appending characters to the end of the base password (e.g. PleaseSubscribe!123) or replacing characters within the base password itself (e.g. Pl3aseSubscr1be!). Fortunately, I found the instructions in the hashcat manual and help page easy to understand and started building a couple of different enumeration commands, and it wasn’t long before one of them was successful.
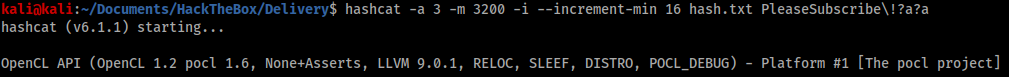
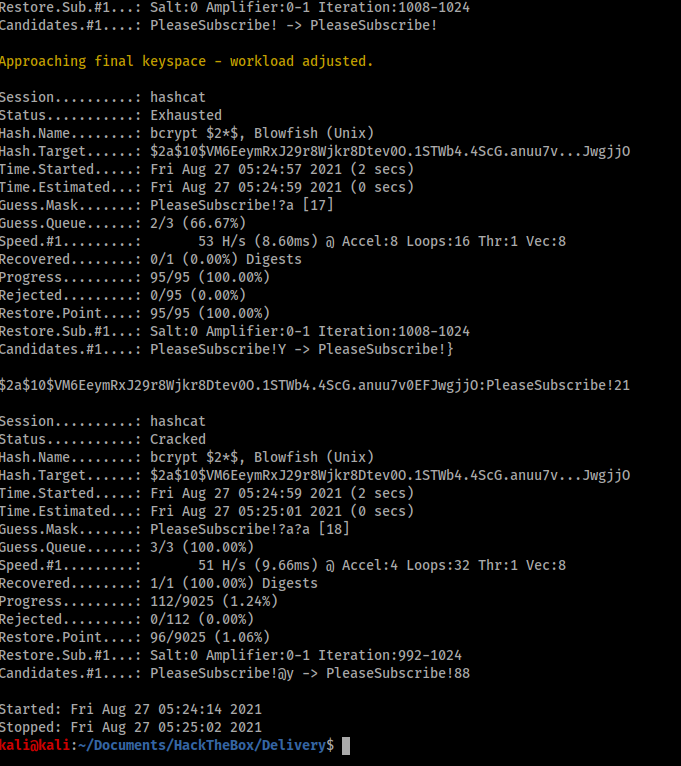
As the shown in the image above hashcat was able to break the hash and reveal the password – PleaseSubscribe!21. With this, I could simply ‘su’ from my existing shell and gain root access.
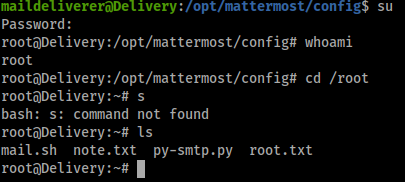

Conclusion
Delivery was a fun box and one that I would highly recommend for beginners. Gaining the user flag required no technical or toolset specific knowledge that might hinder new hackers. Instead, it was easily done by exploiting logic errors in the application. From there, the path to privilege escalation was clearly laid out and required minimal technical know-how, beyond simple MySQL commands. The hardest part of this box was the hashcat commands, however password cracking tools are essential for every hacker so this is a great opportunity to learn one of the most popular ones. Some may claim that the lack of tools and technical knowledge required to hack this box makes it a waste of time, but I contend that this box absolutely has merit in developing the confidence and mindset of new hackers and it is for this reason that I recommend it.