Nibbles is a very straightforward box on Proving Grounds. It is in the “Get To Work” category because it requires two steps to root, however it really is simple enough to be part of the “Warm Up” category and is a great box for beginners looking to practice privilege escalation.
Enumeration
I started with AutoRecon which generated the below nmap result with 6 ports – 21, 22, 80, 139, 445 and 5437.
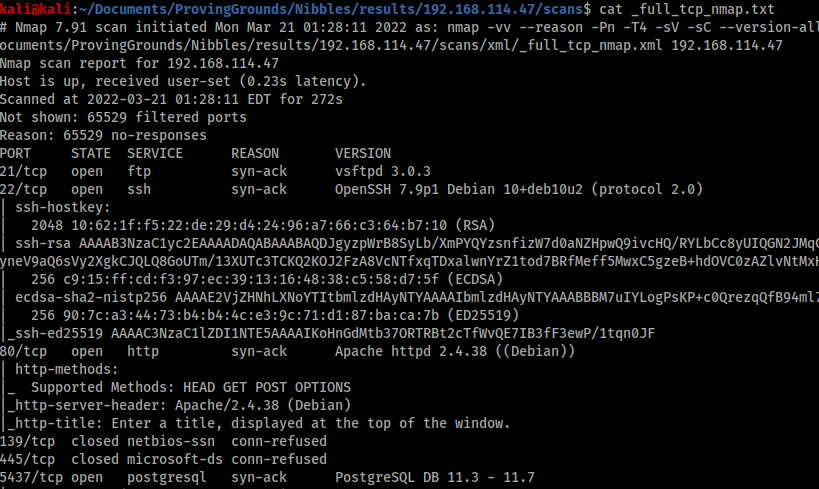
Ports 21 and 80 had no easily identifiable entry points, and 139 and 445 were closed. Port 22 is almost never the way in, so that left 5437 which nmap told me was using PostgreSQL.
Foothold
A quick google search brought up a promising link from Squid22.
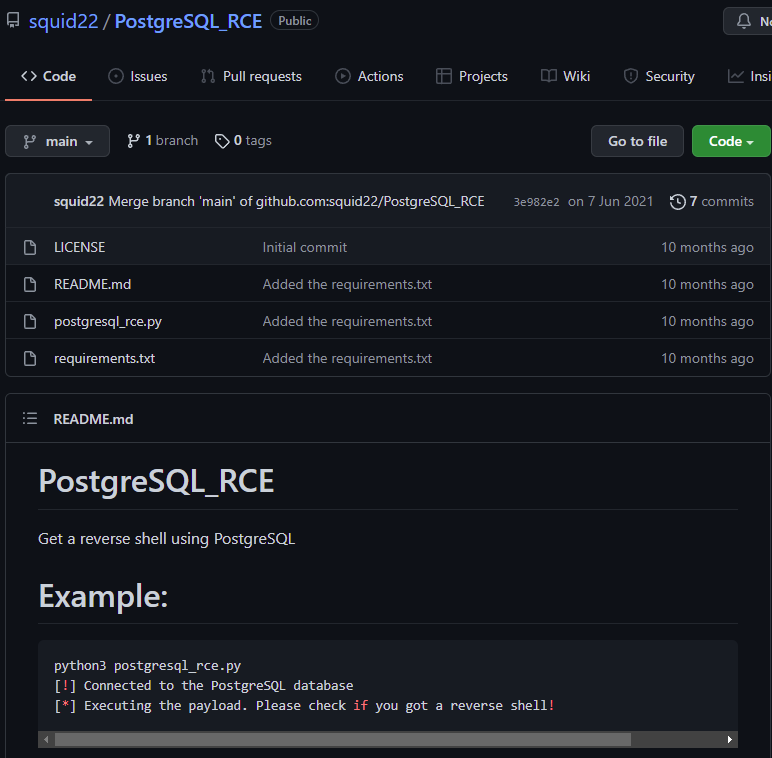
I downloaded the script, pointed it at my target machine, set up a listener on port 80, ran the exploit and got a shell back straight away.

PostgreSQL_RCE exploit

I uploaded LinPEAS using a python server and ran it.


The result was very obvious, the bright yellow highlight from LinPEAS suggesting that the SUID settings of the ‘find’ command could be abused for privilege escalation.

I consulted GTFOBins for the correct command to use.
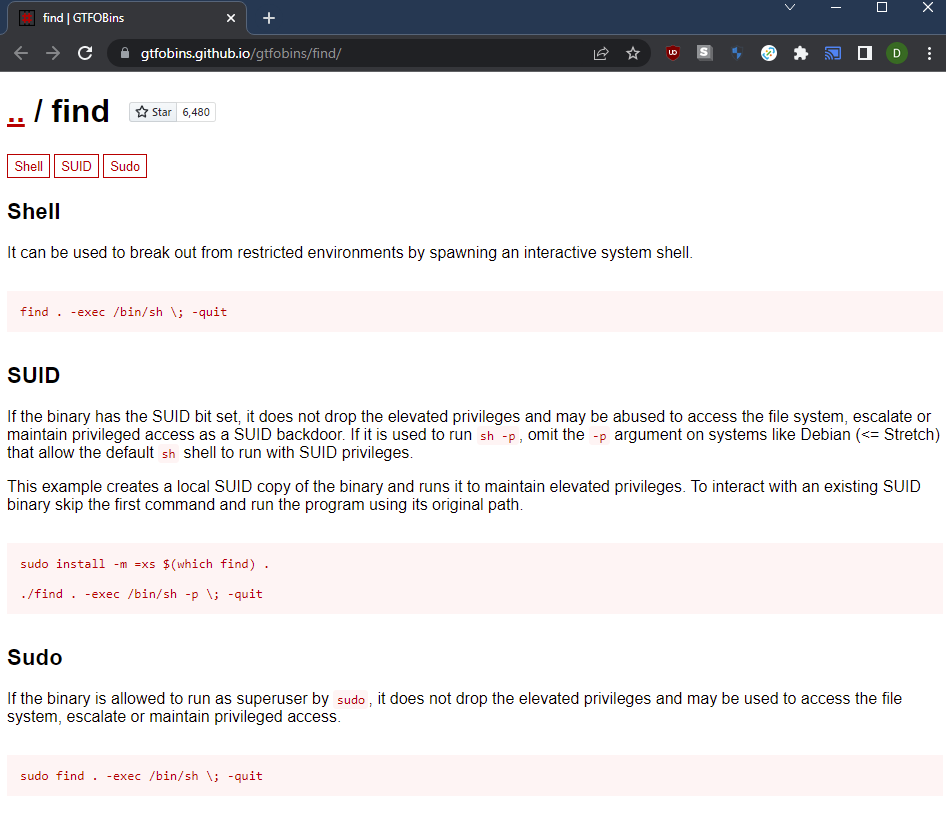
Then I simply ran the command without ‘sudo’ and received a root shell.

Conclusion
Nibbles is a very straight forward box that rewards good enumeration and research. Anyone who has completed the ‘Warm Up’ boxes on Proving Grounds and is starting to try privilege escalation for themselves should consider using Nibbles as good practice for post-foothold enumeration and